WELCOME TO CYBERSECURITY MONTH!
Cybercrimes & Everything You Need to Protect Your Business
October marks the start of Cybersecurity Awareness Month. It started with President George W. Bush in 2004, to help individuals protect themselves online as threats to technology and confidential data become more commonplace. Now it is an annual event held globally every October.
The Cybersecurity and Infrastructure Security Agency (CISA) and the National Cybersecurity Alliance (NCA), working with several partner organizations have put together an extensive program of events for citizens, businesses, and public sector organizations.
The cybercrime business has become one of the most lucrative illegal ventures out there, showing no signs of slowing down. Over the past ten years, hackers have developed new and sophisticated ways of getting their hands on your most important data.
The unfortunate odds are that these cybercriminals will not be caught; meanwhile, consumers continue to face far more significant risks than ever before.
Why Is Cybercrime So Dangerous and Can You Be Safer?
If you are a small business using an off-the-shelf software, I’m sorry to inform you that you are at a higher risk of becoming a victim of cybercrime. We have all, at some point, received phishing emails or have been asked for personal information via our work email from people asking for something out of the ordinary. Most employees have work and personal information on either their company websites or social media. It’s one thing for your business to get scammed, but these bad actors will also go after your clients putting your reputation and business at risk. Fortunately, there are some things that you can do to keep yourself safer.
Social Media Risks
A criminal hacker can target any employee who uses social media. It’s fairly dangerous, but we at Protected Harbor have some tips. We harden our clients’ networks and run employee training all the time. The best thing to tell your employees is to not post anything online that you would not say to your competitors or your manager.
Several social networking sites, such as LinkedIn, allow users to post their resumes. Information concerning one’s work can reveal too much about one’s personal life, giving criminals such as hackers information that may enable them to hack into one’s account. Identity theft can also be committed using resume information.
The privacy settings on most social networking sites are either pre-set or default. Suggest your staff make an effort to alter their privacy settings to block strangers and people who are not friends with them from viewing their private information.
Protecting Yourself from Spyware and Viruses
Think about utilizing safe search online browsing software, frequently included in antivirus software complete editions. This software often uses a red, yellow, or green dot next to the links on the search engine. This aids in warning employees of potentially harmful websites.
Never download a torrent file or a software crack, and never download any file that doesn’t come from a reliable website. These frequently include malware. Also, do not click on any pop-up windows that you are not expecting. Instead, either close the window or get out of your browser completely.
Most importantly, make sure that you are updating your OS’s security patches and always have the latest version of your web browser installed. It sounds simple, but companies like Windows Defender push patches and updates daily to fix vulnerabilities. If you are not fast enough in updating the software, a hacker will use it as an entry point into your system.
Understanding Social Engineering
Generally, social engineering involves some type of deception to gather information to commit fraud or gain access to a computer. For instance, our google account uses Meta for Business to run our Facebook Page. Often, we will get a general email to our work email claiming our ads were blocked or taken down due to a violation. It would be tempting to open the email and click on such a link if we actually ran ads there.
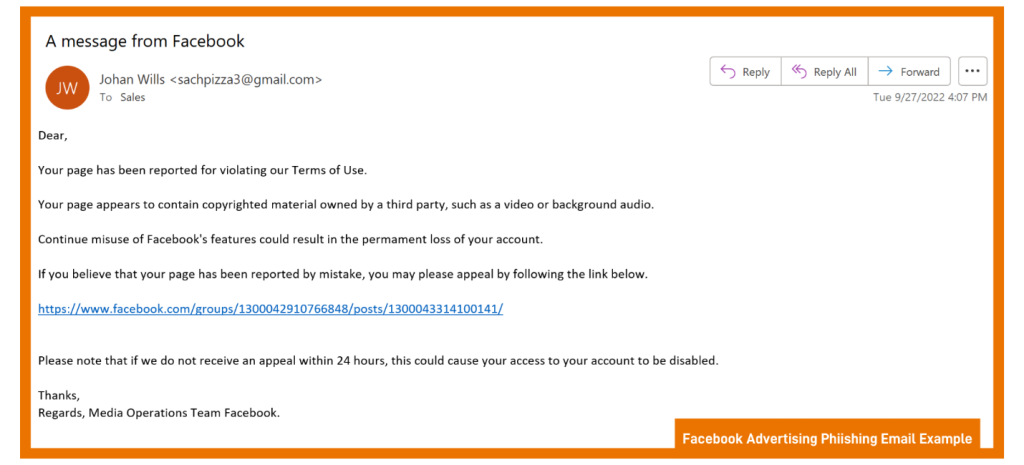
Do you know what typosquatting is? Pay attention to the spelling of website addresses. They may resemble a real website, but instead, they are misspelled, for example, GOOGLE.com vs. G00GLE.com.
Any email including an offer of any kind should raise suspicions, especially if it seems too good to be true. The same applies to receiving offers from social media or reputable internet businesses, like Facebook and Google.
Caller ID Spoofing; What You Need to Know
“ID spoofing,” is another cybercrime you must be aware of. These days, a random phone call is more likely than ever to be a scammer. Criminals can fool people by hiding their information using “spoofing.” Spoofing disguises, the telephone number from which a text is sent by creating a new one. Phony numbers with the same area code are often used to persuade recipients to answer. The scary thing for businesses is that they can make it look like your number, and call clients.
All of your business numbers and extensions represent assets that you need to protect. Software like IntelePeer and Hiya Connect Secure Call can stop scammers from mimicking your phone numbers, regardless of how many lines and extensions you have in your internal network.
Is Public Wi-Fi Safe?
Unfortunately, public Wi-Fi is not secure. Several security risks are associated with using a public Wi-Fi. These networks broadcast signals through radio frequencies, which means that anyone who has the right tools, and these tools are fairly easy to find, can intercept the data that is sent through it.
To protect yourself when using public Wi-Fi, you should use either a remote desktop or virtual desktop. DO NOT USE A VPN!
A VPN (Virtual Private Network) helps you establish a private network while using any public networks. While beneficial to provide access to employees and third parties, this access is open-ended and unsecure. All security capabilities are lost when granting third parties’ remote access via VPN. VPNs lack access controls and session monitoring, both effective means of security for network access. VPNs don’t manage, vault, or verify credentials, so password protection depends on your third parties keeping them safe.
Remote desktop solutions are becoming increasingly familiar with the increased prevalence of distributed workforces and more employees regularly working from home. It’s perfect for people who are either frequently on the go, work out of a home office, or are often out in the field and need access to their local desktop computer. RDP is encrypted by default with a higher level of encryption than VPN and requires no additional connection time.
Even if you have a virtual desktop, don’t store any type of critical data on a device, and then use it outside of a network that is not secure. That means downloading documents to your cellphone, then connecting to Starbucks’ free Wi-Fi to watch TikTok. Turn off the Bluetooth and Wi-Fi on your cell phone or laptop when you aren’t using them, a device that can still send wireless signals appeals to a hacker.
What Is a Credit Freeze?
If you don’t have a credit freeze on your business bank account, you are putting your business at further risk. A credit freeze, sometimes called a security freeze, locks down a credit file so that a lender cannot check your credit. This is a good thing, as criminals cannot open any new accounts using your name or your EIN…and if a lender can’t check your credit, they are unlikely to extend a line of credit.
Remember that you must request a credit freeze from each credit bureau, including Equifax, Experian, Innovis, and TransUnion. Remember you can always un-freeze your accounts whenever needed.
 Keeping Your Passwords Safe and Protected
Keeping Your Passwords Safe and Protected
The most important thing you need to know about passwords is that there is no secure password. Some passwords are more secure than others, of course, but they can always be found. Passwords are extremely convenient for people who want to access your accounts.
Is a Password Manager a Good Idea?
It’s hard to keep track of all your passwords, so it’s tempting to reuse the same one across the board. However, if a hacker gets possession of your password, they’ll have free access to everything you have. Password managers, on the other hand, can simplify your life.
It’s unsurprising for us to be asked, “are password managers safe to use?” The answer is, the use of password managers is considered to be one of the most secure ways to protect your passwords. Password managers offer strong protection against cybercrime because of their encryptions. AES, the industry-standard protection used by the U.S. government to safeguard its sensitive data, is just one example.
Set Up Two Factor Authentication on All Accounts
Password authentication is when a user enters a unique ID and key compared to previously stored credentials. It is one of the quickest forms of security; you can set up your device to require some identification before letting someone access your phone. It can be in a passcode, PIN, password, fingerprint, or two-factor authentication (2FA) can be adopted as well.
An additional layer of protection is provided by 2FA, which ensures that the user is whom they say they are. Before gaining access to the account, the user must first provide their username and password. The second piece of information is then requested. Almost every major company and organization website utilizes some kind of two-step, or two-factor, identification.
Protecting Your Credit Cards
Many of us, especially in today’s world, use credit cards for not only our jobs but even our daily lives, and there are several things you can do to protect yourself from credit card fraud.
First, make sure to examine your business credit card statements often to see whether they include any unfamiliar or strange expenses. Check your credit card accounts weekly if you can. Check for both large and small charges. If the hackers want to make a large purchase, they might make a small purchase to ensure it goes through.
You can also set up “push” alerts on your company accounts to receive notifications via email or text when purchases are made. For example, you may receive a text any time purchase over $100 is made, or an email anytime there is an online credit card transaction.
Also, store your credit card numbers online at your peril. It’s safer to manually enter the digits every time you want to purchase than to auto-input via Google or Apple.
Final Words
Many businesses have already installed firewalls, spam filters, and anti-virus software in order to prevent any cybercriminals from breaking in, yet they are still concerned – and we don’t blame them. These preventions are worthless without a dedicated IT team to respond to malicious attacks and fix compromised devices. If you are worried about ransomware or cyber-attacks, bringing in an experienced team to help with the rise in threats can provide a level of service beyond what firms currently have and at a lower cost.
Outside teams like Protected Harbor bring years of actionable experience to strengthen an organization.
We will ensure that your organization is protected from outside threats with well-tested, proven, and integrated technology. Protected Harbor concentrates on six elements throughout the stack, uplink, firewall, switches, hosts, VMs configuration, and storage to safeguard our customers’ operations.
We are offering free cybersecurity assessments and IT audits to all companies that may be interested. You can sign up here: Free Cybersecurity Assessment