What Iran’s Cyber Attack On Boston Children’s Hospital Means For Your Healthcare Organization
What Iran’s Cyber Attack On Boston Children’s Hospital Means For Your Healthcare Organization
 Wednesday, June 1st, At a Boston College cybersecurity conference hosted by Mintz, FBI Director Christopher Wray stated that investigators prevented a planned attack on Boston Children’s Hospital by Iranian government-sponsored hackers. The FBI director told the story as part of a bigger speech about cyber threats from Russia, China, and Iran, as well as the importance of government-private partnerships.
Wednesday, June 1st, At a Boston College cybersecurity conference hosted by Mintz, FBI Director Christopher Wray stated that investigators prevented a planned attack on Boston Children’s Hospital by Iranian government-sponsored hackers. The FBI director told the story as part of a bigger speech about cyber threats from Russia, China, and Iran, as well as the importance of government-private partnerships.
What Happened
In the summer of 2021, the FBI received a tip from an intelligence partner that hackers sponsored by the Iranian government were targeting the Boston Children’s Hospital. The cyber squad in the FBI Boston Field Office raced to notify the hospital. Over a 10-day period, worked with the hospital in response to the threat
Wray didn’t say why the hospital attack was planned, but he did say that Iran and other governments have been hiring cyber mercenaries to carry out attacks on their behalf. Furthermore, the US government has identified the healthcare and public-health sectors as one of 16 critical infrastructure sectors. Healthcare providers such as hospitals are considered easy targets for hackers.
It wasn’t clear if the hackers planned to target the hospital with ransomware, shut down the hospital operations with a virus, or sell the data on the black market. That’s because the FBI caught the attack early enough to prevent any damage to the network or the hospital’s data. The FBI declined to discuss the specific nature of the attack in detail, citing security reasons.
Nevertheless, the FBI issued a warning in November saying Iranian government hackers had breached the “environmental control network” at an unidentified children’s hospital in the United States last June. Leading many to assume the same was targeted in Boston. The environmental control network refers to the hospital’s HVAC system.
What it Means
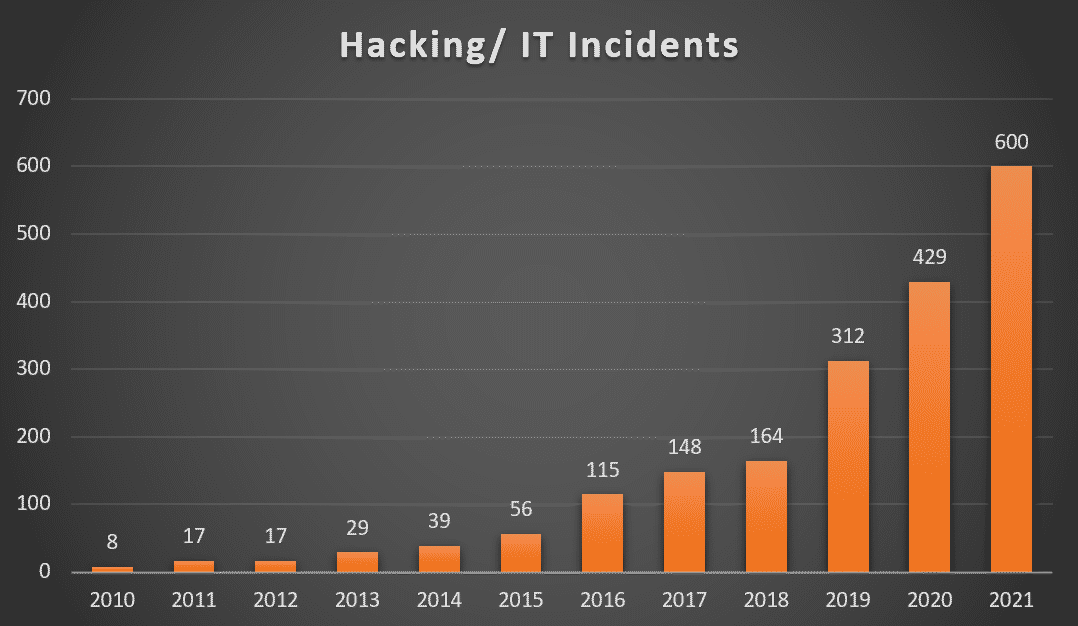
In the case of ransomware, hospitals can face devastating system shutdowns. Patient data can be made inaccessible to hospital staff, it can be damaged, or it can be stolen and sold. A ransomware attack compromised a Vermont hospital’s patient record system in October 2020, and patients have turned away as a result.
Nation-states and hacker groups are probing healthcare organizations and looking for areas to exploit. This past November, the Cybersecurity and Infrastructure Security Agency issued an alert for an Iran-sponsored hacker group targeting healthcare. As the Russia-Ukraine war drags on, federal agencies say U.S. healthcare organizations need to be “shielded up” to mitigate against potential foreign threats.
The FBI is “racing” to warn possible healthcare targets of data breaches when it comes to Russia and other state-sponsored attacks. According to Wray, China’s hackers have stolen more business and personal data from Americans than all other countries combined as part of an enormous geopolitical ambition to “lie, cheat, and steal their way into global denominations of global industries.”
All hospitals and healthcare organizations must sit up and take notice. It is not only hacktivist groups and employees they need to worry about, today. But nation-states as well.
 Protected Harbor’s Take On The Issue
Protected Harbor’s Take On The Issue
Protected Harbor has been monitoring the situation for a long time and continues to emphasize cybersecurity. Richard Luna, CEO of Protected Harbor, said this is a severe issue, and we advise all our clients to take precautionary measures and make sure their systems are secure and protected.
He suggested 3 simple tips to harden your servers, which every company should implement immediately.
1. Update the operating systems on your servers regularly.
The most crucial action you can take to secure your servers is to keep their operating systems up to date. On a nearly daily basis, new vulnerabilities are discovered and publicized, with the potential for remote code execution or local privilege escalation.
2. Enforce The Use Of Strong Passwords
Enforcing the usage of strong passwords across your infrastructure is an important security measure. Attackers will have a harder time guessing passwords or cracking hashes to obtain unauthorized access to sensitive systems. A smart place to start is with 10-character passwords that include a mix of upper and lowercase letters, numbers, and special characters.
Password guessing attacks can be stopped by combining a strong password policy with a powerful account robust policy that locks accounts after a few erroneous tries.
3. Use local protection mechanisms such as firewalls and anti-virus software.
Local protection measures and estate-wide controls like patching, domain configuration, and border fire-walling are critical for offering a defense-in-depth approach.
The chance of unneeded default services being exposed to the broader network is reduced when a host’s local firewall is configured correctly. Even if your patching schedule has fallen behind, it will still prevent an attacker from accessing critical network services. While not fool proof, this all-or-nothing strategy can distinguish between compromise and attacker frustration.
With so much at stake, it’s essential to ensure your business has a robust IT audit plan. With the help of a trusted IT auditing company like Protected Harbor, you can be sure that your systems are secure and functioning at peak efficiency. Because The FBI won’t always be there, but Protected Harbor will.
Sign up to get a risk-free IT Audit and see how you can improve your security. We will analyse your business from top to bottom and give recommendations on making your company safer. What are you waiting for? Get Protected!






 Wellstar Health System announced on Friday afternoon that its email system had been hacked.
Wellstar Health System announced on Friday afternoon that its email system had been hacked. Use Encryption
Use Encryption

 Patient Data Theft: High risk
Patient Data Theft: High risk
