How to Prevent IT Issues Before They Happen

How to Prevent IT Issues Before They Happen
A major concern for CTOs and IT managers in today’s fast-paced digital landscape is how to prevent IT issues before they happen. Imagine a world where costly downtimes and disruptive technical glitches are a thing of the past. This comprehensive guide dives into proactive strategies to tackle potential IT problems head-on, ensuring your systems run smoothly and efficiently. Join us as we answer How to prevent IT issues before they happen and explore the best practices to safeguard your IT infrastructure and keep your business on the path to success.
Understanding IT Issues
Information Technology (IT) issues can range from minor glitches to significant system failures. These problems can stem from hardware malfunctions, software bugs, network disruptions, or cybersecurity threats. Understanding the root causes of these issues and IT risk management is the first step in preventing them.
1. Proactive IT Management
What is Proactive IT Management?
Proactive IT management involves anticipating potential IT issues and addressing them before they escalate into significant problems. This approach focuses on regular maintenance, monitoring, IT security, and updating systems to ensure they run smoothly.
Benefits of Proactive IT Management
Proactive IT management offers numerous benefits, including prevent IT downtime, increased productivity, cost savings, and improved security. By addressing issues before they occur, businesses can maintain seamless operations and avoid disruptions.
2. Regular System Maintenance
Importance of Regular Maintenance
Regular system maintenance is essential for preventing IT issues. This includes updating software, patching vulnerabilities, and ensuring that hardware components are functioning correctly. Regular maintenance helps identify and resolve potential problems before they impact operations.
Key Maintenance Activities
Key maintenance activities include:
- Updating operating systems and software applications
- Patching security vulnerabilities
- Cleaning and organizing hardware components
- Running diagnostic tests to identify potential issues
3. Monitoring and Alerts
Implementing Monitoring Tools
Implementing monitoring tools is crucial for proactive IT management. These tools continuously monitor systems for signs of potential issues, such as unusual activity, performance degradation, or security threats. Early detection allows for swift resolution, preventing minor issues from becoming major problems.
Setting Up Alerts
Setting up alerts is an effective way to stay informed about potential IT issues. Alerts can be configured to notify IT staff of unusual activity, performance drops, or security threats. Prompt notifications enable quick action to mitigate risks.
4. Security Measures
Importance of Cybersecurity
Cybersecurity is a critical aspect of preventing IT issues. Cyber threats, such as malware, ransomware, and phishing attacks can cause significant disruptions, data breaches and IT security issues. Implementing robust security measures is essential for protecting IT infrastructure. It’s important to have a data backup and recovery plan in place.
Key Security Practices
Key security practices include:
- Installing and updating antivirus software
- Implementing firewalls and intrusion detection systems
- Educating employees about cybersecurity best practices
- Conducting regular security audits and assessments
5. Employee Training
Training for IT Awareness
User training and awareness are crucial for preventing IT issues. Educating staff about potential IT problems, cybersecurity threats, and best practices for using IT systems can significantly reduce the risk of issues. Well-informed employees are less likely to make mistakes that could lead to IT problems.
Continuous Learning
IT risk management and continuous learning and development programs ensure that employees stay updated on the latest IT trends and threats. Regular training sessions and workshops can help maintain a high level of IT awareness within the organization.
6. Network Optimization
Importance of Network Optimization
Network optimization is crucial for preventing IT issues related to connectivity and performance. A well-optimized network ensures that data flows smoothly and efficiently, reducing the risk of slowdowns and disruptions.
Strategies for Network Optimization
Strategies for network optimization include:
- Regularly updating network hardware and software
- Implementing quality of service (QoS) settings to prioritize critical traffic
- Monitoring network performance and addressing bottlenecks
- Ensuring adequate bandwidth and capacity planning
 7. Software Management
7. Software Management
Managing Software Updates
Managing software updates is essential for preventing IT issues. Keeping software applications up to date ensures that they are secure and functioning correctly. Regular updates with IT risk management also provide new features and improvements that enhance productivity.
Software Version Control
Implementing software version control helps manage updates and changes effectively. Version control systems track changes to software code, allowing for easy rollback in case of issues. This ensures that updates are implemented smoothly without causing disruptions with proper data backup and recovery in place.
8. Hardware Management
Maintaining Hardware Health
Maintaining hardware health is crucial for preventing IT issues. Regularly inspecting and servicing hardware components can identify potential problems before they lead to failures. This includes cleaning, replacing worn-out parts, and ensuring proper ventilation.
Upgrading Hardware Components
Upgrading hardware components when necessary ensures that IT systems remain efficient and capable of handling increasing workloads. Timely upgrades can prevent performance bottlenecks and extend the lifespan of IT infrastructure.
9. Third-Party Audits
Conducting IT Audits
Conducting third-party IT audits provides an unbiased assessment of your IT infrastructure. Audits can identify potential IT security issues, vulnerabilities, and areas for improvement. Regular audits help ensure that IT systems are secure and functioning optimally.
Implementing Audit Recommendations
Implementing audit recommendations is crucial for addressing identified issues and improving IT infrastructure. Following through on audit findings ensures that potential problems are resolved before they impact operations.
10. Incident Response Planning
Developing an Incident Response Plan
Developing an incident response plan is essential for managing IT issues effectively. An incident response plan outlines the steps to take in case of IT problems, ensuring that issues are addressed quickly and efficiently.
Testing the Response Plan
Regularly testing the incident response plan ensures that it is effective and up to date. Conducting drills and simulations helps identify weaknesses and areas for improvement, ensuring that the plan is ready for real-world scenarios.
11. Remote Monitoring and Management (RMM)
Benefits of RMM
Remote Monitoring and Management (RMM) tools provide real-time monitoring and management of IT systems. RMM tools offer numerous benefits, including early detection of issues, automated maintenance tasks, and remote troubleshooting.
Implementing RMM Solutions
Implementing RMM solutions involves selecting the right tools and configuring them to monitor your IT infrastructure effectively. RMM tools provide valuable insights into system performance and potential issues, enabling proactive management.
12. Predictive Analytics
Using Predictive Analytics
Using predictive analytics involves analyzing data to identify patterns and trends that indicate potential IT issues. Predictive analytics can provide early warnings of hardware failures, performance issues, and security threats, allowing for proactive intervention.
Implementing Predictive Maintenance
Implementing predictive maintenance involves using data and analytics to schedule maintenance tasks before issues arise. This approach ensures that systems are maintained in optimal condition, reducing the risk of unexpected failures.
Correlation of Events and Its Importance in IT Management
Event correlation involves analyzing IT events to identify patterns and root causes, enabling faster response and reduced downtime. Building systems with efficient event correlation in mind ensures structured data collection and automated analysis, allowing IT security teams to quickly address issues and maintain smooth operations. This proactive approach significantly enhances IT management, minimizing disruptions and improving overall system reliability.
How to prevent common IT issues in small businesses
Preventing IT issues in small businesses starts with regular maintenance and proactive strategies. Key IT problem prevention steps include updating software consistently to close security gaps and ensure compatibility. Backing up data frequently, both locally and to the cloud, safeguards against data loss. Implementing strong IT maintenance tips—such as scheduling antivirus scans, monitoring system performance, and managing hardware lifespans—helps prevent unexpected failures. Use IT issue prevention strategies like network segmentation and multi-factor authentication (MFA) to enhance security and mitigate risks. Training employees on cybersecurity basics is also critical, as many breaches stem from user errors. Together, these practices help prevent IT downtime, keeping systems efficient and secure, and reducing costly interruptions for small businesses.
Conclusion
Preventing IT issues before they happen is crucial for maintaining smooth and efficient operations. By implementing proactive IT management strategies, businesses can reduce downtime, improve productivity, and enhance security. Regular maintenance, monitoring, employee training, and leveraging advanced tools like RMM and predictive analytics are key to staying ahead of potential IT problems.
At Protected Harbor, we specialize in proactive IT management to ensure your systems run seamlessly. As a top Managed Service Provider New York, we are dedicated to preventing IT issues before they happen by implementing robust security measures, regular maintenance, and continuous monitoring. Let us help you safeguard your IT infrastructure and keep your business running smoothly. Contact us today to learn more about our proactive IT solutions and how we can support your business.





 Best Practices for Proactive IT Monitoring
Best Practices for Proactive IT Monitoring


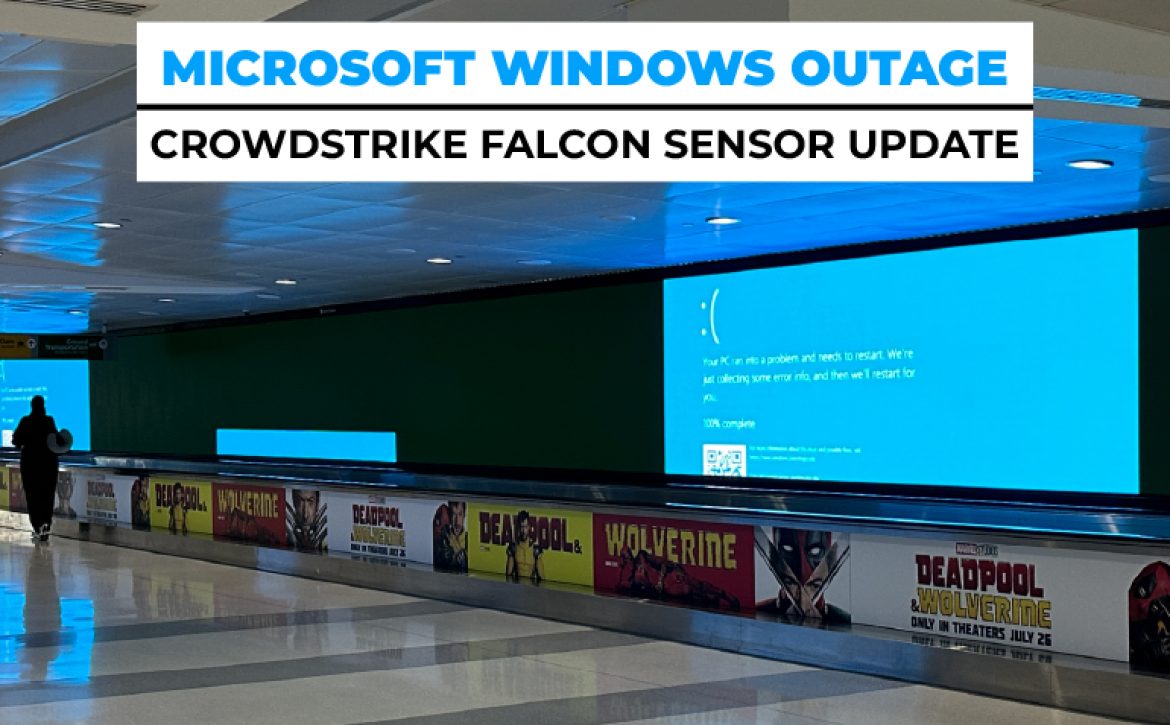
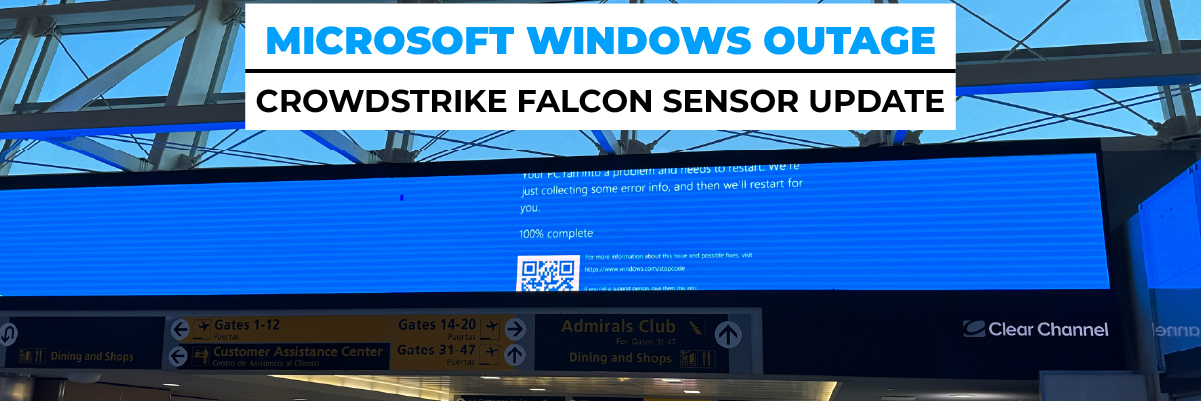
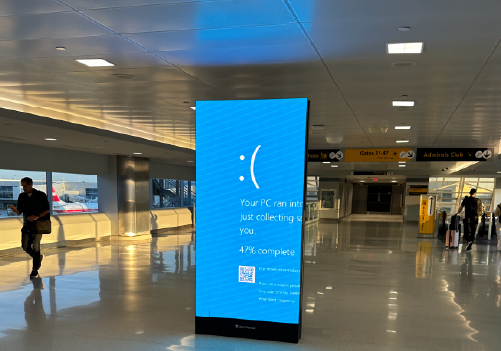

 4. Disaster Recovery and Business Continuity
4. Disaster Recovery and Business Continuity




 Advanced AI Capabilities in ITOps
Advanced AI Capabilities in ITOps
 Challenges and Considerations
Challenges and Considerations

 Additional Key Features
Additional Key Features