What is an Incident Response Plan (IRP) Checklist?
What is an Incident Response Plan (IRP) Checklist?
An Incident Response Plan is your best bet for protecting your company from the consequences of a data breach. The time to plan and prepare for security crises is NOW, whatever they may be, long before they occur.
What is an Incident Response Plan?
A cybersecurity incident response plan (IR plan) is a set of guidelines designed to assist businesses in preparing for, detecting, responding to, and recovering from network security problems. Most IR strategies are tech-focused, addressing concerns like malware detection, data theft, and service disruptions. However, any sizeable cyber assault can have a wide-ranging impact on a firm; therefore, the plan should include finance, customer service, HR, employee communications, legal, and other outside entities.
Why is Incident Response Plan Important?
An Incident Response Plan is important because it defines how to reduce the length and severity of security incidents and identify stakeholders, streamline digital forensics, enhance recovery time, and prevent unfavorable publicity and customer attrition.
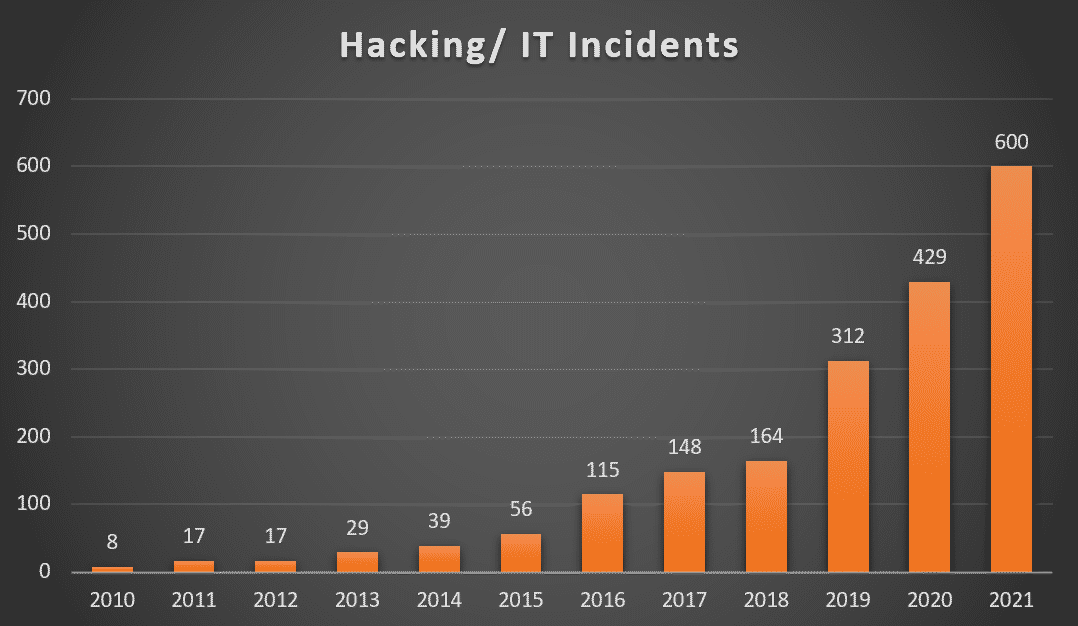
Small cybersecurity mishaps, such as malware infection, can quickly escalate into more significant issues, resulting in data breaches, data loss, and company interruption.
A good incident response procedure will help your company reduce damages, patch exploitable vulnerabilities, restore affected systems and processes, and close the attack vector.
Incident response is essential for preventing future occurrences and maintaining a company that handles sensitive data like PII, PHI, or biometrics.
IRP Audit
Before writing your Incident Response Plan, you should conduct a security audit of your company. This will help you identify weak areas. You should also identify who is responsible for the incident and determine who will handle the incident. In addition, you should define the parties involved and who will handle it.
Creating an IRP should include several key stakeholders, such as representatives from different company areas, including outside PR. In addition to the team members, it should also include the CEO, board members, and PR representatives. The process should be transparent and approved by key stakeholders easy to implement, but it should not be overly complex. It must be simple to understand, and it should be based on a multi-tiered approach.
How to create an Incident Response Plan & Checklist?
Create an Incident Response Plan
- The first and most important step in incident response planning is preparation. It should include defining the roles of the IR team and creating an underlying security policy. The security policy should identify the locations and relative value of sensitive data, as well as how many IT resources your company needs to respond to an attack. Make sure that your executives are on board with the plan before it goes live.
- The second step in creating an Incident Response Plan (IRP) is testing. It is critical to test the IRP to ensure that all components are working correctly. The purpose of testing is to determine whether the plan is effective and whether the team can handle the incident effectively. The IRP must be supported by upper management. The plan must be able to prevent or mitigate a security breach. It must be easy to implement, and it should be quick to execute.
- The final step in creating an Incident Response Plan is to define the response, the incident, or the event that will trigger it. There are many types of incidents, and different responses must be developed for each. Your IRP should identify the kind of security incident likely to occur and identify responsible parties. In addition, you should include a comprehensive communication plan, including the methods and frequency of communication with the affected parties.
Creating an incident response plan checklist can help your staff cope with a significant incident. IR Plan checklist is made keeping in mind what should be done after an incident.
Post-Incident– The ultimate step of an incident response plan is to create a post-incident investigation checklist. This checklist should include various information, such as disk images, logs, and network traffic reports. It should also detail key elements, including entry point, root cause analysis, and organizational resources targeted in the aftermath of an incident. After the investigation is complete, the team should recommend changes to prevent the same occurrence from occurring again.
Recovery– A recovery phase focuses on bringing systems back to normal operation. The response team must notify affected parties of the nature and extent of the attack within a specified period, such as 72 hours for GDPR. Once the system has been returned to production, the team needs to perform necessary tests, validate that it is operating normally, and document the process. The entire process should take a minimum of a day, depending on the size of the IT network and the business operation.
The recovery phase involves bringing affected systems back to production and testing them regularly. A well-developed plan should include these processes. The more specific they are, the better your plan will be. The more thorough and comprehensive your plan is, the more effective it will be.
Conclusion
The purpose of our cyber incident response plan checklist is to assist your IT security team in developing a complete, coordinated, repeatable, and effective incident response strategy.
Please remember that creating a cybersecurity incident response plan is never a one-time task. Unfortunately, enterprises and their IT security teams may find themselves outmaneuvered by hackers who pivot in their attack strategies/TTP and malware choice if they do not engage in frequent incident response training and IR exercises, including real cyber assault scenarios.
This article should provide you with the information and resources you need to design and implement a successful incident response plan. Partner with Protected Harbor to add best-in-class behavioral analysis to all of your essential data repositories and infrastructure to ensure your data is safe.
At Protected Harbor, we work with individual customers on an Incident Response Plan (IRP) and help them perform an audit to determine where they are today within their IRP. We follow the Critical Controls and guide our customers that match their Incident Response Plan with the specific controls. This provides them with the ability to have a real improvement plan in place.
With that being said, don’t miss out on other crucial aspects of data protection that can be included in your checklist—things like protected data center, disaster recovery plan, backups, testing, and so on. Contact us to create an IRP which is best for you.









 Patient Data Theft: High risk
Patient Data Theft: High risk












