It is becoming more difficult to prevent ransomware attacks, event large IT departments can have difficulty, just ask Sony, the City of Baltimore, or the City of Atlanta.
For the last 40 years, we have built networks and office systems with the concept of sharing data. Shared folders for example make it easy for users to exchange and edit documents, but also those shared folders are the target of Ransomware attacks.
Some tools can be added to reduce the likelihood of ransomware, but nothing can be purchased to “protect” a company.
The most effective protection for Ransomware starts with a network and desktop redesign followed by layers of security and isolated backups. The best approach is not to try to protect against Ransomware, it is to develop a plan that minimized the impact of an attack. Unfortunately, many of the steps listed below require a desktop or office changes and many organizations are unwilling to change.

The Protected Harbor Difference
At Protected Harbor we will not onboard a client without making the changes needed to protect against Ransomware. We think a new reality is that only good network design and good governance can keep networks safe. Most small IT companies are ill-equipped to understand the depth of the risk, much less take the necessary steps to protect against Ransomware.
The end-user resistance to change combined with tight IT budgets and the concept that IT is low cost has created a climate of a one-stop drop-in application or solution to stop all IT problems. This approach will not work to stop Ransomware. In short at Protected Harbor we protect our clients through better design.

Ways to PROTECT YOUR SYSTEM FROM RANSOMWARE
Below are the steps we take to protect our clients and we recommend the steps are deployed by all organizations.
Desktop/Network & Backup Isolation
The first step in a new network design is to limit through segmentation the network. Desktops, Servers and the backup should all be on separated and isolated networks. Using this approach an infected desktop will not be able to access the backups and will not infect the backups.
Virtualization
Protected Harbor will accomplish desktop and network isolation using virtualization. Virtualization allows Protected Harbor to back up the entire desktop, not just shared folders, or databases, or scanned folders, but all folders. This means we can recover the entire office, and not pieces of the office.
Email & Web Filtering
Filtering of email and web content is an important part of the Protected Harbor Ransomware defense. Good email filtering should include pattern recognition. The initial Ransomware attacks follow a template and email filtering systems when properly configured either block or quarantine the attack.
Enable network monitoring
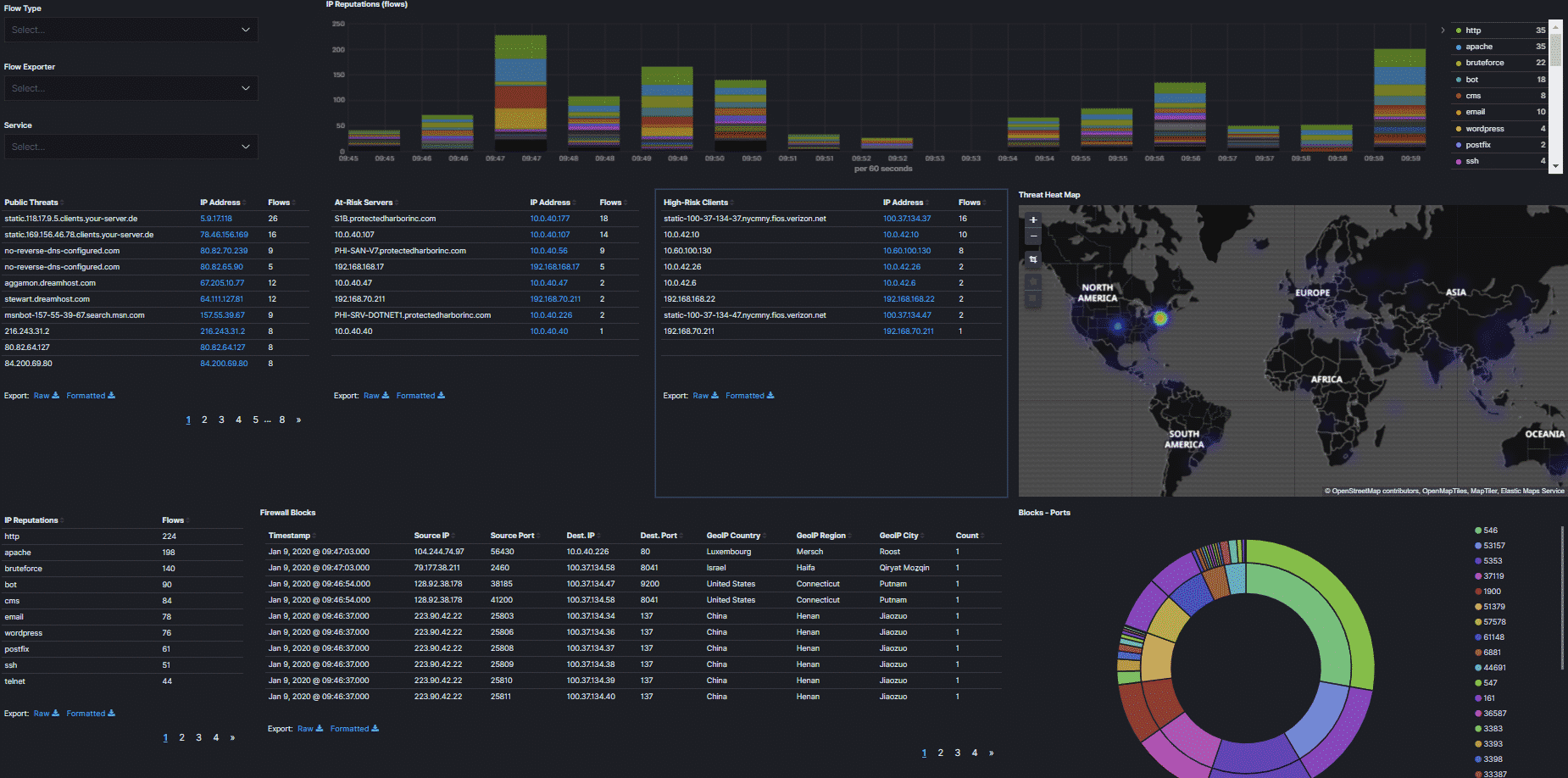
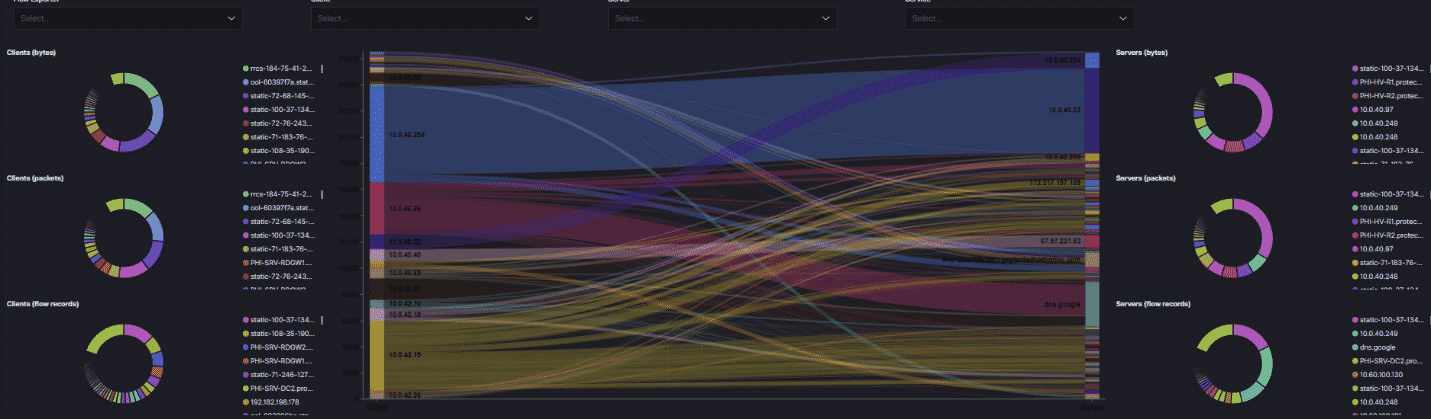
We monitor for inbound and outbound traffic, which allows us to react to attack patterns in addition to standard monitoring. Network monitors can alert and warn on unusual traffic, or traffic that is typical of an attack; for example, if certain information is transmitted out of the network that would trigger an alert. We protect our customers by constantly monitoring network traffic, especially activity to or from parts of the world that are high sources of attacks, for example, Russia or China. We also monitor and alert on traffic flow. Oftentimes, if an end-user connects an infected phone or laptop to the network, we will see a change in the traffic flow which will trigger an alert.
Tighten local server/desktop permissions
Our clients do not run their programs as Administrators. Enhancing the security drastically reduces a ransomware attack and virtually eliminates malware attacks. Enhanced security reduces what an attack can affect through better design.
Reduce the number of common shares folders
Typically, clients will have one or two shared folders that all users have access to. Ransomware attacks not only infect those shares but then use them to spread the attack to other non-infected systems. We work with clients to reduce or eliminate shared folders, increasing the protection through better design to ransomware.
Reduce public corporate contact information
Live email addresses should not be published on a website. If a website needs an email address, the published address shouldn’t use the same format as the internal address. If jsmith is the email prefix, as in jsmith@abc.com then for the website the published email should be jacksmith@abc.com. Additionally, sensors can be added to the content filter for petersmith@abc.com for example. This would mean the attacking IP (the one attempting to send email to petersmith@abc.com) is really a robot attacker; adding that IP to the block list would prevent all future attacks from occurring.
Parameter or Geo Blocking
For our clients we maintain enhanced network protection that includes active parameter checking and Geo-Blocking. For example, we check the address of inbound requests, and if the IP is from a blocked country, then the traffic is blocked even before it reaches the client’s network. Countries we routinely block are North Korea, Russia and countries are known for sending out Ransomware attacks. If access is needed from a blocked country, a simple support ticket resolves the issue.
Testing & Training
At Protected Harbor we perform routine simulated Ransomware attacks. These tests are productive at helping end user stay vigilant to attacks and the tests allow end users to be identified that might need some additional assistance to understand the importance of being careful with email.