How to Safeguard Sensitive Client Information

How to Safeguard Sensitive Client Information
In today’s hyper-connected digital landscape, safeguarding sensitive client information is more crucial than ever. Cyberattacks are on the rise, and data breaches can cause significant financial and reputational damage to businesses. As a leading Managed Service Provider (MSP) and cybersecurity expert in the U.S., Protected Harbor understands the critical need for robust data protection measures. This blog will guide you on how to safeguard sensitive client information and through the practical strategies to ensure client data security, helping your business stay compliant, secure, and trustworthy.
Understanding the Importance of Client Data Protection
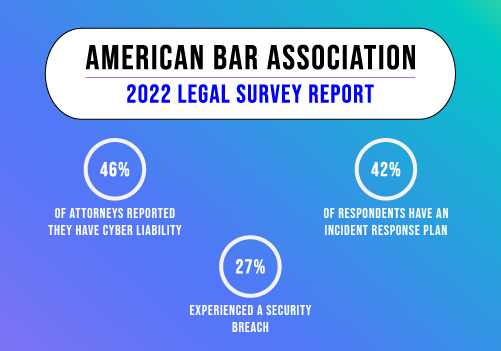
Sensitive client information—ranging from personal identification details to financial records—is a prime target for cybercriminals. A breach not only jeopardizes this information but also erodes trust, leading to long-term consequences such as regulatory penalties, client attrition, and loss of business reputation.
Ensuring your clients’ data security is not just a regulatory requirement; it’s a cornerstone of client satisfaction and business longevity.
Why Protecting Client Data is Crucial
Sensitive client information includes personal, financial, or proprietary data entrusted to your business. A breach can have far-reaching consequences:
- Financial Loss: Data breaches cost businesses millions in fines, legal fees, and operational downtime.
- Loss of Trust: Once a client’s trust is compromised, regaining it is incredibly difficult.
- Regulatory Non-Compliance: Laws like GDPR, HIPAA, and CCPA impose strict requirements for data handling and severe penalties for violations.
Data protection isn’t just about avoiding risks—it’s about fostering client trust and building a reputation for reliability.
Top Strategies to Safeguard Sensitive Client Information
1. Implement Strong Access Controls
Sensitive data should only be accessible to authorized individuals. Use these measures:
Role-Based Access Control (RBAC): Assign permissions based on job roles to ensure that employees only access the data they need.
Multi-Factor Authentication (MFA): Require a second layer of authentication, such as a code sent to a mobile device, to enhance login security.
Time-Based Access: Limit access to specific time frames for users who only need temporary permissions, such as contractors or third-party vendors.
2. Adopt End-to-End Encryption
Encrypting data at rest and in transit ensures that sensitive information remains unreadable to unauthorized parties. Whether it’s email communication or stored client records, end-to-end encryption acts as a vital safeguard against breaches.
3. Regularly Update and Patch Systems
Outdated software is a common vulnerability that hackers exploit. Keep your systems and applications updated with the latest patches and security updates. An automated patch management solution can streamline this process for maximum efficiency.
4. Educate Employees on Cybersecurity Practices
Human error remains a leading cause of data breaches. Equip your employees with the knowledge to recognize and respond to threats:
- Phishing Awareness Training: Teach employees how to identify phishing emails and suspicious links.
- Password Best Practices: Encourage the use of strong, unique passwords and password management tools.
- Data Handling Policies: Ensure employees understand how to handle sensitive information securely, including when working remotely.
Regular training sessions and simulated phishing tests can reinforce good cybersecurity habits.
5. Conduct Regular Security Audits
Periodic security audits help identify vulnerabilities and areas for improvement in your data protection strategy. Tools like penetration testing and vulnerability scans can provide actionable insights to bolster your defenses.
 6. Backup Data Frequently
6. Backup Data Frequently
Maintaining secure backups of client information is essential for disaster recovery. Use encrypted backups stored in a secure, offsite location, ensuring quick restoration in the event of a breach or system failure.
7. Monitor and Respond to Threats Proactively
A robust threat detection and response system can mitigate risks before they escalate:
- 24/7 Monitoring: Use tools that continuously monitor your network for anomalies and potential threats.
- Intrusion Detection Systems (IDS):Identify and flag suspicious activities in real-time.
- Incident Response Plans: Develop and test an incident response plan to address breaches swiftly and minimize damage.
8. Control Data Sharing and Storage
The way data is shared and stored significantly impacts its security:
- Secure File Sharing Tools: Avoid using unsecured platforms to share sensitive information. Opt for encrypted file-sharing services.
- Cloud Security: If using cloud storage, ensure it’s configured with security features like encryption and access controls.
- Data Minimization: Only collect and retain the data you need to reduce exposure risks.
A clear data-sharing policy reduces the likelihood of accidental leaks.
9. Leverage Advanced Cybersecurity Solutions
Partnering with an experienced MSP like Protected Harbor gives you access to cutting-edge cybersecurity tools, including firewalls, intrusion detection systems, and endpoint protection. These solutions proactively safeguard your network against sophisticated threats.
Complying with Data Protection Regulations
Adhering to regulations like GDPR, HIPAA, and CCPA is critical for businesses handling sensitive client data. Compliance not only mitigates legal risks but also demonstrates your commitment to data security. Partnering with an MSP ensures you meet these regulatory standards with ease.
The Role of Protected Harbor in Data Security
With over a decade of experience in MSP and cybersecurity services, Protected Harbor specializes in delivering customized solutions that empower businesses to protect their sensitive client information. Our comprehensive services include:
- Advanced threat detection and response systems
- Proactive monitoring and regular audits
- Robust data encryption and backup solutions
By partnering with us, you’ll gain access to cutting-edge technology and expert support, allowing you to focus on growing your business while we handle your security.
Conclusion
Safeguarding sensitive client information is a non-negotiable priority in today’s digital age. By implementing robust access controls, adopting encryption, and partnering with experts like Protected Harbor, your business can build a resilient data security framework. Protecting your clients’ trust is paramount—don’t leave it to chance.
Take action today! Partner with Protected Harbor to fortify your business against cyber threats. Contact us now for a free cybersecurity assessment and take the first step towards a safer future.





 Detecting Zero-Day Vulnerabilities
Detecting Zero-Day Vulnerabilities












 Additional Security Measures for Law Firms
Additional Security Measures for Law Firms

 Common Examples of IOCs
Common Examples of IOCs
 Threat Detection and Response Best Practices
Threat Detection and Response Best Practices