HIMSS 2025: Shaping the Future of Healthcare Technology with Protected Harbor

HIMSS 2025: Shaping the Future of Healthcare Technology with Protected Harbor
Join Protected Harbor at HIMSS 2025 – Booth 1675
Key Highlights:
- Event Date: March 3-6, 2025 | Location: Las Vegas, NV
- Venue: The Venetian Convention & Expo Center, Caesars Forum, and Wynn Las Vegas
- Protected Harbor Booth: 1675
- Speaking Engagement: CEO Richard Luna
The Healthcare Information and Management Systems Society (HIMSS) Conference 2025 is the premier global event for healthcare innovation and technology. From March 3-6 in Las Vegas, thousands of industry professionals will gather to explore the latest advancements, discuss critical challenges, and collaborate on shaping the future of healthcare.
Why Attend HIMSS 2025?
HIMSS 2025 is designed to provide healthcare leaders with cutting-edge insights and hands-on experiences to drive transformation in digital health, cybersecurity, AI integration, and more. Attendees will have access to keynote presentations, interactive forums, and emerging technology showcases.
Must-Attend Sessions and Keynote Speakers
HIMSS 2025 features a diverse lineup of thought leaders who will share their expertise on:
- Digital Health Transformation: How emerging technologies are revolutionizing patient care.
- Cybersecurity Challenges & Solutions: Strategies to safeguard healthcare data in a digital world.
- AI in Healthcare: Practical applications and responsible AI adoption.
- Interoperability & Data Exchange: Enhancing collaboration across healthcare systems.
Exciting keynote speakers include:
- Dr. Seung-woo Park, President of Samsung Medical Center, discussing digital health transformation.
- General Paul M. Nakasone, former Commander of U.S. Cyber Command, addressing AI and cybersecurity in healthcare.
- Hal Wolf & Dr. Meong Hi Son, leading a discussion on balancing technological advancements with human-centered care.
Key Themes and Focus Areas of HIMSS 2025
HIMSS 2025 will emphasize pioneering advancements and critical topics shaping healthcare technology. The event will feature dedicated forums designed to foster collaboration and address industry challenges.
Pre-Conference Forums:
- AI in Healthcare Forum: Explore strategies for responsible AI implementation in healthcare.
- Healthcare Cybersecurity Forum: Learn from real-world cyber threats and discover methods to strengthen cybersecurity defenses.
- Interoperability and HIE Forum: Gain insights into the regulatory, strategic, and technical aspects of seamless data exchange.
- Nursing Informatics Forum: Examine how nursing informatics contributes to patient-centered care and innovation.
- Smart Health Transformation Forum: Leverage advanced analytics and technology to transition from reactive to proactive healthcare models.
- AMDIS/HIMSS Physicians’ Executive Forum: Collaborate with clinical leaders to improve patient care and digital healthcare strategies.
- Health Equity Forum: Develop actionable strategies to promote healthcare accessibility and reduce disparities.
- Behavioral Health Forum: Uncover best practices and technology solutions for mental health and addiction treatment.
- Public Health Data Modernization Forum: Explore initiatives in modernizing healthcare data infrastructure for public health advancement.
General Conference Sessions
HIMSS 2025 will feature peer-reviewed sessions covering fundamental and emerging healthcare transformation topics, including:
- Core and foundational health IT systems.
- Digital health technologies and maturity.
- Strategies for digital health transformation.
- Emerging healthcare technologies and enterprise imaging.
This year’s event will also showcase innovative approaches to integrating Electronic Medical Records (EMR) and advanced platforms like DARWIN, balancing AI integration with a patient-centric approach, and strengthening health IT infrastructure to counter cybersecurity risks.
Additional discussions will highlight workforce challenges, healthcare automation, global policy shifts in healthcare IT, and disruptive innovations featured in the Emerge Innovation Experience.
Protected Harbor at HIMSS 2025 – Booth 1675
As a leading provider of managed IT and cybersecurity solutions, Protected Harbor is proud to be part of HIMSS 2025. Visit us at Booth 1675 to:
- Discover our innovative approach to cybersecurity and compliance in healthcare IT.
- Engage with our experts for tailored risk management strategies.
- Learn how our 24/7 monitoring and proactive security measures can keep your organization safe.
Experience the Emerge Innovation Zone
This year, HIMSS introduces the Emerge Innovation Experience, where startups and tech pioneers will showcase breakthrough solutions. From AI-driven patient engagement tools to advanced threat detection in cybersecurity, this is the space to witness the next wave of healthcare technology.
Secure Your Spot – Register Now!
HIMSS 2025 is the must-attend event for healthcare professionals looking to stay ahead in an industry undergoing rapid transformation. Don’t miss this opportunity to engage with experts, discover innovations, and network with like-minded professionals.
🔹 Register now to be part of the future of healthcare technology! 🔹 Visit Booth 1675 and connect with the Protected Harbor team.











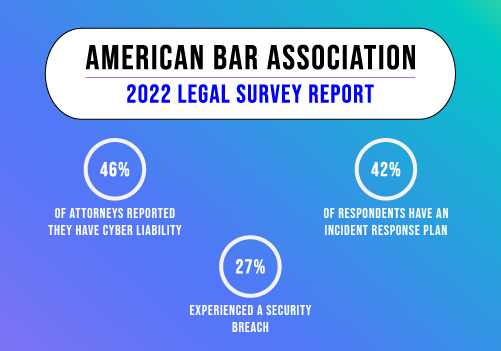
 The certification for SOC 2 comes from an independent auditing procedure that ensures IT service providers securely manage data to protect the interests of an organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a Software as a Service (SaaS) provider. Developed by the American Institute of CPAs (AICPA), SOC 2 defines criteria for managing customer data based on five “trust service principles” – security, availability, processing integrity, confidentiality, and privacy.
The certification for SOC 2 comes from an independent auditing procedure that ensures IT service providers securely manage data to protect the interests of an organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a Software as a Service (SaaS) provider. Developed by the American Institute of CPAs (AICPA), SOC 2 defines criteria for managing customer data based on five “trust service principles” – security, availability, processing integrity, confidentiality, and privacy.