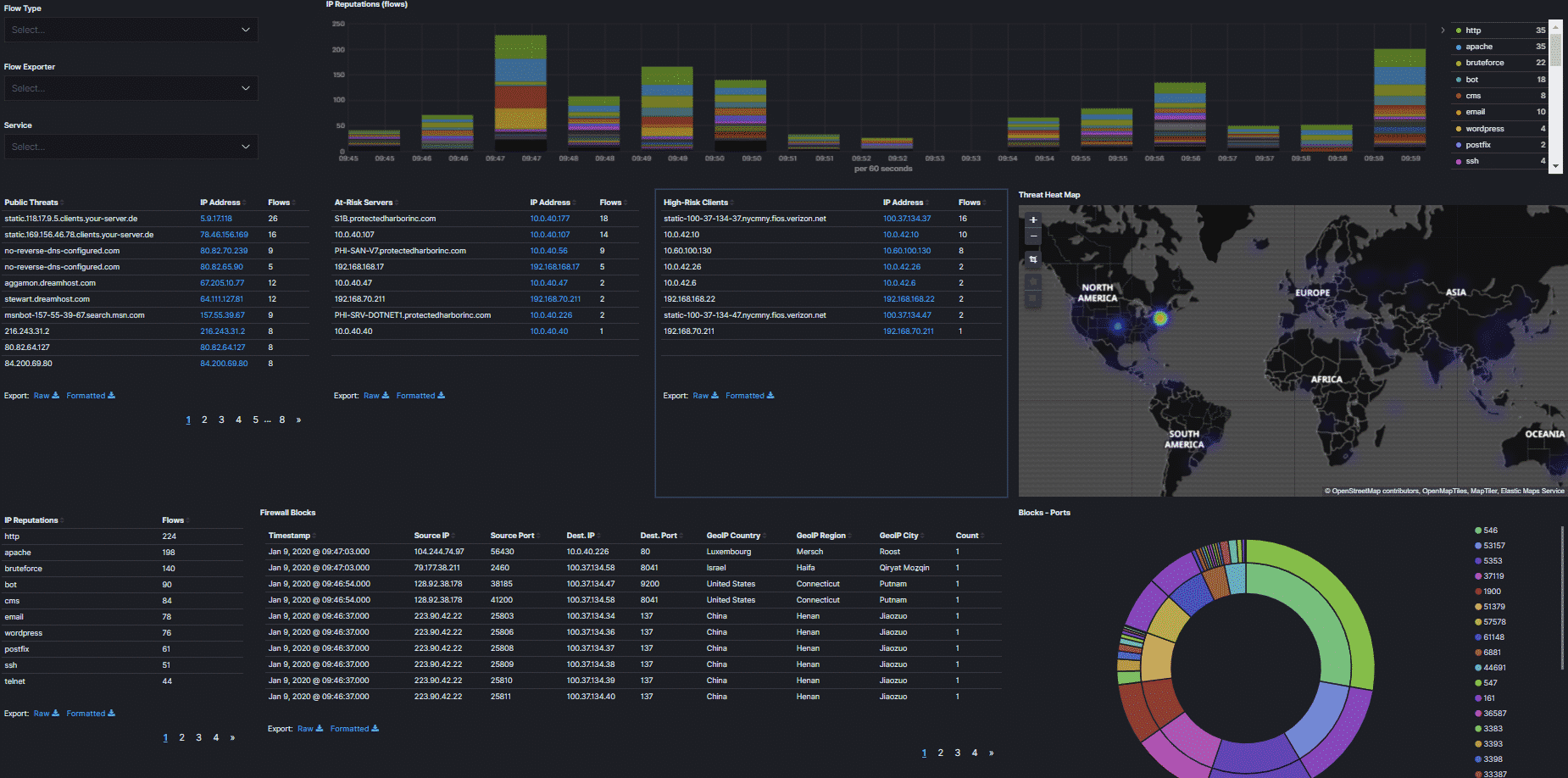
What varieties of viruses and ransomware are there?

What are the different types of viruses and ransomware?
In this digital age, viruses and ransomware are becoming a growing security concern for computer users. The threat of malicious software is real, and understanding the different types of viruses and ransomware is essential to protect yourself and your data. There are four main types of viruses, each with its own characteristics and potential harm. These include Trojans, bots, malware, and ransomware. With some basic knowledge, computer users can better protect themselves against these malicious programs. Knowing the differences between these types of viruses and their capabilities is the first step to keeping your computer safe and secure.
Virus:
A computer virus is a malicious code or program written to alter how a computer operates and is designed to spread from one computer to another. A virus operates by inserting or attaching itself to a legitimate program or document that supports macros to execute its code. In the process, a virus can potentially cause unexpected or damaging effects, such as harming the system software by corrupting or destroying data.
Two types of viruses causing headaches for security experts are multipartite virus and polymorphic virus. Multipartite viruses leverage multiple attack vectors to infiltrate systems, while polymorphic viruses cunningly change their code to evade detection. Understanding and defending against these sophisticated adversaries is crucial to safeguarding our digital world.
A macro virus is a malicious code quickly gaining popularity amongst hackers. It is a type of virus that replicates itself by modifying files containing macro language, which can replicate the virus. These can be extremely dangerous as they can spread from one computer to another and can cause damage by corrupting data or programs, making them run slower or crash altogether. Users need to take preventive measures against the threat of viruses, as they can eventually cause serious damage.
Worm:
A computer worm is a type of malware that spreads copies of itself from computer to computer and even operating system. A worm can replicate itself without any human interaction and does not need to attach itself to a software program to cause damage.
Ransomware:
The idea behind ransomware, a form of malicious software, is simple: Lock and encrypt a victim’s computer or device data, then demand a ransom to restore access.
In many cases, the victim must pay the cybercriminal within a set amount of time or risk losing access forever. And since malware attacks are often deployed by cyber thieves, paying the ransom doesn’t ensure access will be restored.
Ransomware holds your personal files hostage, keeping you from your documents, photos, and financial information. Those files are still on your computer, but the malware has encrypted your device, making the data stored on your computer or mobile device inaccessible.
Who are the targets of ransomware attacks?
Ransomware can spread across the Internet without specific targets since it’s one of the most common types of computer virus. But this file-encrypting malware’s nature means that cybercriminals can also choose their targets. This targeting ability enables cybercriminals to go after those who can — and are more likely to — pay larger ransoms.
Trojan:
A Trojan horse, or Trojan, is a type of malicious code or software that looks legitimate but can take control of your computer. A Trojan is designed to damage, disrupt, steal, or inflict some other harmful action on your data or network.
A Trojan acts like a bona fide application or file to trick you. It seeks to deceive you into loading and executing the malware on your device. Once installed, a Trojan can perform the action it was designed for.
A Trojan is sometimes called a Trojan or a Trojan horse virus, but that’s a misnomer. A Trojan cannot. A user has to execute Trojans. Even so, Trojan malware and Trojan virus are often used interchangeably.
Bots:
Bots, or Internet robots, are also known as spiders, crawlers, and web bots. While they may be utilized to perform repetitive jobs, such as indexing a search engine, they often come in the form of malware. Malware bots are used to gain total control over a computer.
The Good
One of the typical “good” bots used is to gather information. Bots in such guises are called web crawlers. Another “good” use is automatic interaction with instant messaging, instant relay chat, or assorted other web interfaces. Dynamic interaction with websites is yet another way bots are used for positive purposes.
The Bad
Malicious bots are defined as self-propagating malware that infects its host and connects back to a central server(s). The server functions as a “command and control center” for a botnet or a network of compromised computers and similar devices. Malicious bots have the “worm-like ability to self-propagate” and can also:
- Gather passwords
- Obtain financial information
- Relay spam
- Open the back doors on the infected computer
Malware:
Malware is an abbreviated form of “malicious software.” This is software specifically designed to gain access to or damage a computer, usually without the owner’s knowledge. There are various types of malware, including spyware, ransomware, viruses, worms, Trojan horses, adware, or any malicious code that infiltrates a computer.
Each type of malware has its own purpose and potential impacts, making it important to be aware of the different types of malware. We can protect ourselves from these malicious software threats with the right knowledge and resources.
Generally, the software is considered malware based on the creator’s intent rather than its actual features. Malware creation is rising due to money that can be made through organized Internet crime. Originally malware was created for experiments and pranks, but eventually, it was used for vandalism and destruction of targeted machines. Today, much malware is created to make a profit from forced advertising (adware), stealing sensitive information (spyware), spreading email spam or child pornography (zombie computers), or extorting money (ransomware).
The best protection from malware — whether ransomware, bots, browser hijackers, or other malicious software — continues to be the usual preventive advice: be careful about what email attachments you open, be cautious when surfing by staying away from suspicious websites, and install and maintain an updated, quality antivirus program.
Spyware:
Spyware is unwanted software that infiltrates your computing device, stealing your internet usage data and sensitive information. Spyware is classified as a type of malware — malicious software designed to gain access to or damage your computer, often without your knowledge. Spyware gathers your personal information and relays it to advertisers, data firms, or external users.
Spyware is used for many purposes. Usually, it aims to track and sell your internet usage data, capture your credit card or bank account information, or steal your personal identity. How? Spyware monitors your internet activity, tracking your login and password information, and spying on your sensitive information.