Mother of All Breaches Exposes 26 Billion Records

Mother of All Breaches Exposes 26 Billion Records from Twitter, LinkedIn, and More!
In a shocking revelation, the cybersecurity world is grappling with what experts are calling the “Mother of All Breaches.” A colossal leak has laid bare 26 billion records, including those from internet giants like LinkedIn, Snapchat, Venmo, Adobe, and the former Twitter, now known as X. This unprecedented breach has ignited concerns about widespread cybercrime and the potential for devastating consequences on a global scale.
The compromised data extends beyond mere login credentials; it includes a trove of “sensitive” information, raising alarms among cybersecurity experts. The dataset’s sheer breadth and depth make it a goldmine for malicious actors, enabling a spectrum of cyber threats such as identity theft, sophisticated phishing schemes, targeted cyberattacks, and unauthorized access to personal and sensitive accounts.
Cybernews, the first to discover this catastrophic breach on an unsecured website, emphasizes the gravity of the situation. “The dataset is extremely dangerous,” warns cybersecurity expert Bob Dyachenko and the Cybernews team. “The majority of the population has likely been affected.”
One silver lining, however, is that the 12 terabytes of data appear to be a compilation of previously stolen information rather than newly acquired data. Cybernews believes it may be a meticulous aggregation of various breaches, making it a so-called “COMB.”
The records that have been made public are from a variety of platforms, with Tencent—the massive Chinese instant messaging company—leading the list with 1.4 billion hacked records. There were additional notable data leaks on Weibo, MySpace, Twitter, Deezer, and LinkedIn. Among the victims are well-known websites like Adobe, Telegram, and Dropbox as well as lesser-known ones like Doordash, Canva, Snapchat, and even international governments.
Protected Harbor’s CEO, Luna, Weighs In:
In response to this cyber Armageddon, Protected Harbor’s CEO, Protected Luna, expressed deep concern about the potential fallout. Luna emphasized the need for swift action and heightened security measures in light of the breach:
The “Mother of All Breaches” exposed today, serves as a sobering reminder of the ongoing dangers that exist in the digital sphere. We must take the initiative to protect our digital identities as stewards of sensitive data. Protected Harbor urges everyone to act right away by changing their passwords, using two-factor authentication, and being watchful for phishing efforts. Our combined defense is essential in this digital age to lessen the effects of such massive breaches.
Leaked Data Includes Passwords
The revelation of the “Mother of All Breaches” underscores a harrowing reality: the compromised data extends far beyond superficial details. Among the 26 billion records laid bare, the inclusion of passwords has set off alarm bells within the cybersecurity community. This treasure trove of leaked data presents a grave threat to data privacy, amplifying concerns about unauthorized access, information leaks, and the proliferation of sophisticated cyber threats.
The exposed passwords once considered a bastion of digital security, now serve as ammunition for malicious actors seeking to exploit vulnerabilities. This grim reality underscores the critical importance of robust security measures and vigilant cybersecurity practices to thwart potential phishing schemes, targeted cyberattacks, and other nefarious activities facilitated by the leaked data. As individuals and organizations grapple with the aftermath of this unprecedented breach, safeguarding sensitive information and fortifying defenses against cyber threats emerge as imperative priorities in the ongoing battle to preserve data privacy and mitigate the risks of unauthorized access.
Here’s What LinkedIn Has to Say
In response to the “Mother of All Breaches,” LinkedIn has acknowledged the significant impact of data exposure and emphasized its commitment to data privacy in cyber security. A LinkedIn spokesperson stated, “We take the security of our members’ data very seriously. Our team is actively investigating about the information leaked on dark web and taking necessary steps to ensure the safety of our platform.”
LinkedIn advises all users to:
1. Change Passwords Immediately: Ensure new passwords are strong and unique.
2. Enable Two-Factor Authentication (2FA): Add an extra layer of security to your account.
3. Be Wary of Phishing Attempts: Stay cautious of unsolicited messages and links.
4. Monitor Account Activity: Regularly check for any suspicious activity.
LinkedIn continues to work closely with cybersecurity experts to address the breach, the most common cyber attacks and safeguard its users’ data. For more information and updates, visit LinkedIn’s Security Center.
Real-life Examples of Major Data Breaches and Their Impact
In recent years, major data breaches have significantly impacted companies and their stakeholders. In 2017, Equifax experienced a breach that exposed the personal information of 147 million people, including Social Security numbers and addresses. Detected in July 2017, the breach had begun months earlier, costing Equifax around $1.4 billion and severely damaging its reputation. Similarly, Yahoo faced two substantial breaches in 2013 and 2014, compromising the data of all 3 billion users. The breaches, disclosed in 2016, included names, email addresses, and phone numbers, leading to a $350 million reduction in its sale price to Verizon and highlighting weaknesses in Yahoo’s security systems. These incidents underscore the critical importance of timely data breach detection and robust cybersecurity measures to protect sensitive information and maintain consumer trust.
Act Now
This breach’s unprecedented scope has shrunk all previous records and established new standards for cyber threats. Following the Mother of All Breaches, consumers need to continue being cautious and implement cybersecurity best practices. Enhancing digital defenses requires regularly changing passwords, putting two-factor authentication into place, and keeping up with emerging threats.
Working with a strong cybersecurity solution is essential in the face of growing cyber threats. With Protected Harbor as your shield against the cyber storm of vulnerabilities, secure your digital future. For cutting-edge cybersecurity solutions, go to Protected Harbor.





 Additional Security Measures for Law Firms
Additional Security Measures for Law Firms

 Myth #3: Two-Factor Authentication is Infallible – No Need for Additional Security Measures
Myth #3: Two-Factor Authentication is Infallible – No Need for Additional Security Measures
 Threat Detection and Response Best Practices
Threat Detection and Response Best Practices

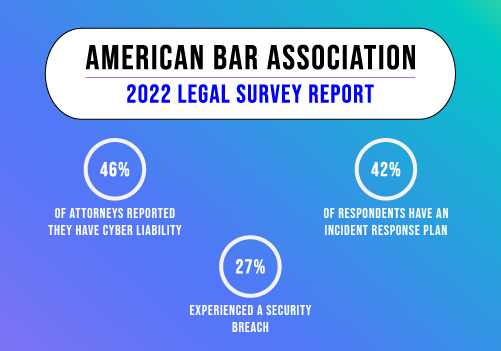



 6. Regularly Update Software and Systems
6. Regularly Update Software and Systems