How does I.T. Support Student Success

How does I.T. Support Student Success?
The role of information technology (I.T.) in supporting student success has become increasingly important in modern educational institutions. From online course management systems to virtual learning environments, I.T. plays a vital role in the day-to-day operations of educational establishments. It is no surprise, then, that an increasing number of universities and schools are investing in the latest I.T. infrastructure to support the learning and development of their students.
All online educational techniques are referred to as digital education. According to projections, the global e-learning market is expected to reach 243 billion U.S. dollars by 2022. The demand for self-paced e-learning products was worth 46.67 billion dollars in 2016 and is expected to fall to 33.5 billion dollars in 2021. A sizeable portion of academic staff worldwide has demonstrated a desire to support modern, digital education paradigms.
Higher education institutions are replacing traditional resources with educational technologies to stay up with their population of digital learners due to the adoption of remote learning. This article provides an overview of the role of I.T. in supporting student success, including the different types of I.T. services available and how they can be used to enhance the learning experience. By exploring the latest tools and technologies available, institutions can ensure that their students can access the resources they need to achieve their academic goals.
Technology as a Bridge Connecting Students and School
Technology has become an integral part of the educational system. It is used for many things, such as distance learning, teleconferencing, and video conferencing. The use of technology in schools has made it easy for students to learn from anywhere in the world.
The use of technology in teaching has been a big success and has helped many students gain knowledge. Teachers must incorporate technology into their lessons and activities to make the most of this opportunity. This way, they can reach out to more people and teach them at a greater level of proficiency.
Schools are already using technology in innovative ways across multiple platforms such as apps, e-books, and social media platforms like Facebook and Twitter. These tools allow teachers and administrators to engage with students in previously impossible ways — especially when it comes to supporting those who may need extra assistance. At the same time, they’re out of school because of illness or other reasons beyond their control (such as family obligations).
 Role of I.T in Student Success
Role of I.T in Student Success
Below are some ways to implement a student approach using innovative technology in the classroom to boost student success and promote engagement.
Help with Online Education
Students can learn at home or on their schedule with the right tools. If you’re unfamiliar with software programs like Moodle, which is used for online education, ask your school district about the available resources. You may even be able to get training from a local organization such as the American School Counselor Association (ASCA).
Data Security of Student Records
Schools should ensure that all student data is secure and that students can access their files whenever needed. Check with your school district about how this information will be kept safe on their computers and storage systems. It’s also essential that parents understand this information because if they don’t know what’s going on with their child’s information, they could be missing out on crucial learning opportunities!
Cleaned Up Every Summer & Winter Break
During the summer and winter breaks, students are away from school and often at home with family members or friends. It’s easy for distractions to creep into online life too! This can lead to poor grades on assignments or missed deadlines for projects due in class.
Active Participation
Students can now participate more actively in their educational experience because of technology. They no longer follow what is written in the book; instead, they are much more motivated to research other issues independently. Technology gives them the freedom they need to do so. This encourages active engagement, significantly increasing their interest in their subjects.
In-Class Tech Support
In-class tech support is crucial for students struggling with issues or questions during class. There are many ways a teacher can provide tech support in their classroom; however, one of the most popular methods is using Google Classroom. This application allows teachers to create assignments and assign them to students, automatically sending out notifications for problems or errors during class. Students will receive email notifications if there is an error with their assignment or if it needs to be rescheduled at another time due to lack of attendance or other issues.
Networking and Internet
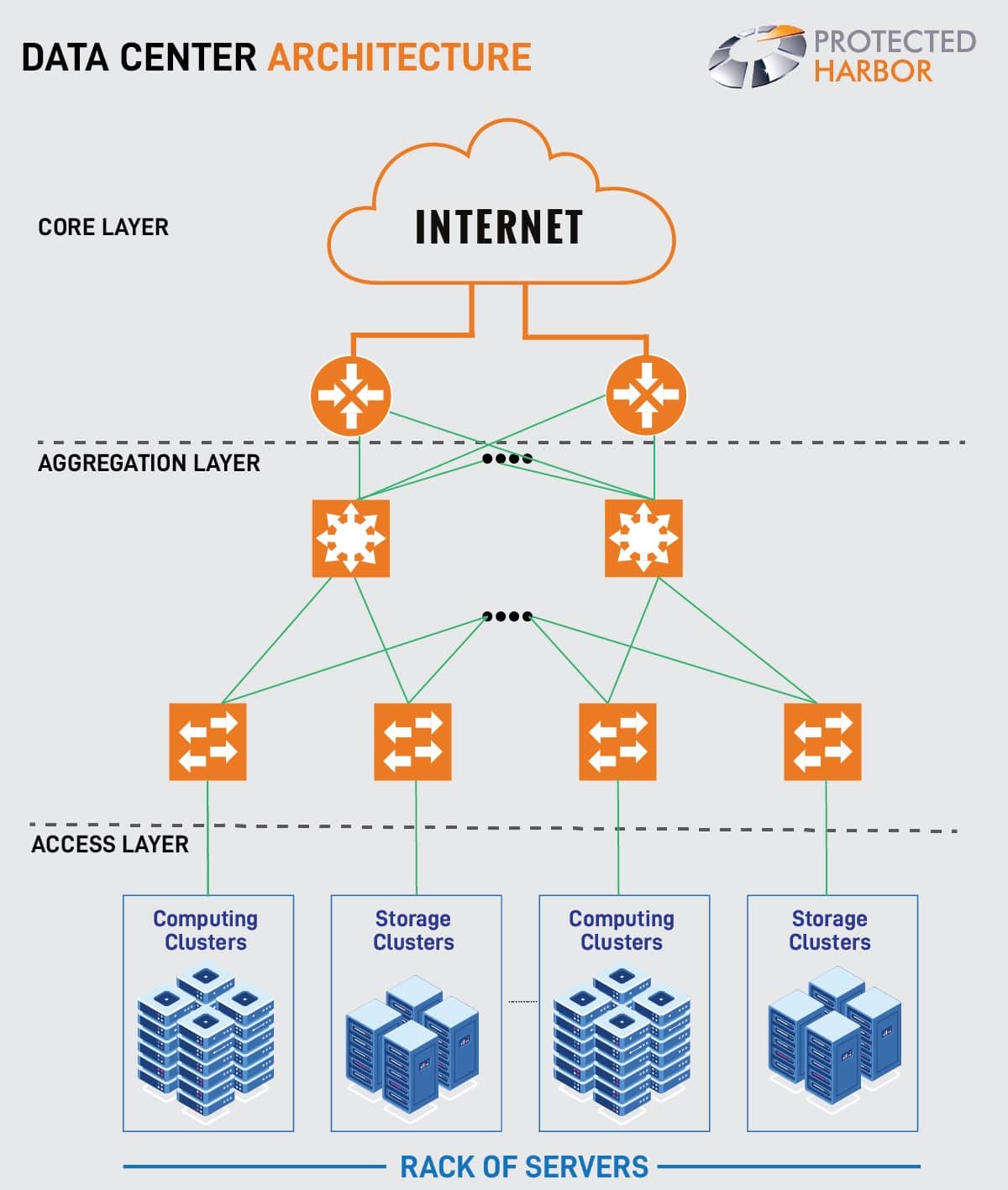
Networking is a critical component of any educational institution’s technology infrastructure. Ensuring students have access to the internet, reliable connectivity, and wireless networks that meet their needs is essential for student success (and teacher retention).
It helps Connect Students to the Real World
I.T. can help students make connections between the natural world and the classroom. Many students had no experience with computers or the internet before starting high school. This can make it difficult for them to find ways to apply their knowledge in the real world. I.T. provides opportunities for students to engage with technology, which will help them become more well-rounded individuals who are prepared for college and career success beyond high school graduation day.
Help Desk for Teachers and Parents
A help desk for teachers and parents will help ensure everyone can access the student Chromebook whenever needed, regardless of where they are in the world. It’s an easy way to ensure students get access to their materials while ensuring teachers and parents can provide support when they need it most.
Increases the Enjoyment Element of Learning
Students use technology in every part of their lives outside of the classroom. Technology can enhance the learning experience in the school. Teachers can use interactive games and leaderboards to give lessons using teaching strategies like game-based learning (GBL). Does anyone enjoy playing games? Insight tools can be used to gather feedback and evaluate the effectiveness of these gamification activities, allowing you to go beyond anecdotal evidence and determine the true efficacy of these new technologies. Monitoring these initiatives is an excellent illustration of organizational adaptability in action.
Conclusion
As you can see, technology plays a huge role in education and has an increasing impact. However, because many conventional teaching methods should continue to be used, it is essential to use technology in education properly. It is up to educators to create a balance between preparing students for the future and the good old-fashioned offline classroom. Also, school management needs to be more crucial about security while e-learning.
With the ever-changing landscape of information technology, the education industry must stay ahead of the curve to provide the best service for its students. This is especially true for K-12 schools, which must meet strict data security requirements to keep student data safe. Protected Harbor Consulting provides schools with the best of both worlds — high-quality data security and low-cost solutions. It is a comprehensive solution for all educational institutions to manage their IT infrastructure, software, and content.
Employing I.T. experts like Protected Harbor saves you much hassle. The solutions they offer can help you have a risk-free learning environment. Get a free IT Audit and learn how we support student success.






 Most Common Exposure Points for Cloud-based Applications
Most Common Exposure Points for Cloud-based Applications




 Email Providers
Email Providers













 In this rapidly evolving threat landscape,
In this rapidly evolving threat landscape,