What’s Indicator of Compromise (IOC) in Cybersecurity

Understanding Indicator of Compromise (IOC) in Cybersecurity
In today’s interconnected digital world, cybersecurity has become a paramount concern for individuals, businesses, and governments. The increasing frequency and sophistication of cyberattacks necessitate a proactive and vigilant approach to safeguarding digital assets. To combat these threats effectively, it’s crucial to understand and leverage advanced tools and techniques. One such tool in the cybersecurity arsenal is the Indicator of Compromise (IOC).
In this blog, we will delve deep into the world of IOCs and explore how they play a pivotal role in fortifying our digital defenses. Whether you’re a cybersecurity professional looking to enhance your knowledge or someone curious about the mechanisms behind cyber threat detection, this comprehensive guide will provide you with the insights you need.
What is an Indicator of Compromise (IOC)?
An Indicator of Compromise (IOC) is a vital concept in cybersecurity. It is a specific piece of evidence or information that indicates a potential security breach, a malware signature or a compromised state within a computer system, network, or organization. IOCs are used to detect, identify, and respond to cyber threats and incidents. They serve as “red flags” that cybersecurity professionals and systems can use to recognize and investigate suspicious activities.
How do Indicators of Compromise work?
Indicators of Compromise (IOCs) are digital clues—like unusual network traffic or modified files—that signal a potential security breach. Used in intrusion detection systems, IOCs help cybersecurity teams identify, investigate, and respond to threats early. These markers are essential in cybersecurity incident response, enabling experts to detect suspicious behavior quickly, analyze the breach, and implement protective measures. By monitoring IOCs, organizations strengthen their defenses and minimize damage from cyber threats, ensuring a proactive security stance.
Types of IOCs
- Host-based IOCs: These indicators are associated with a specific endpoint or host system, such as a computer or server. Host-based IOCs can include unusual system file changes, unauthorized processes running, or suspicious log entries on an individual machine.
- Network-based IOCs: These indicators are related to traffic and communication patterns. Network-based IOCs can include unusual data flows, unexpected port activity, or connections to known malicious IP addresses or domains.
- File-based IOCs: These indicators are centered around files or software. File-based IOCs can involve detecting malicious files by examining their digital fingerprints, such as checksums or cryptographic hashes. Suspicious file names or file paths are also considered file-based IOCs.
Most Common Indicators of Compromise (IOCs)
- Unusual Outbound Network Traffic
Suspicious patterns in outbound network traffic can be one of the first signs of a compromise. Since this traffic originates from inside the network, it is easier to monitor. When IT teams spot irregularities, it’s crucial to investigate immediately to identify potential threats before data is exfiltrated. - Anomalies in Privileged User Account Activity
Privileged accounts have access to sensitive areas of the network, making them prime targets. Unexpected activity, such as privilege escalation attempts or accessing higher-level accounts, can signal an attack early, helping to prevent damage. - Geographical Irregularities
Logins from unusual locations, especially countries where your organization doesn’t operate, can indicate unauthorized access by malicious actors. - Other Login Red Flags
Multiple failed login attempts by an existing user or attempts to access non-existent accounts can suggest a brute-force attack. - Spikes in Database Read Volume
An unexpected surge in database reads could indicate that an attacker is attempting to exfiltrate data, a typical malware signature for data theft. - Abnormal HTML Response Sizes
If HTML responses suddenly show much larger sizes, it could indicate bulk data extraction by an attacker. - Repeated Requests for the Same File
Multiple requests for the same file may signal a hacker’s attempt to find a way to steal sensitive data. - Mismatched Port-Application Traffic
Using uncommon ports can indicate an attacker trying to exploit specific applications or bypass security controls. - Suspicious System File or Registry Changes
Malware often modifies system files or registry settings. Monitoring for such changes and comparing them to known malware signatures can help detect a compromise early. - DNS Request Anomalies
Command-and-Control (C&C) servers often use unusual DNS requests to communicate with infected systems. Detecting unusual patterns, especially from unexpected geolocations, is key to identifying malware activity.
Significance of IOCs in Cybersecurity
IOCs play a critical role in cybersecurity for several reasons:
- Early Detection: IOCs serve as early warning signs with intrusion detection system, that an intrusion or compromise may have occurred. Detecting IOCs promptly allows organizations to respond swiftly, minimizing potential damage.
- Incident Response: When IOCs are identified, they trigger cybersecurity incident response actions. Cybersecurity teams can investigate the incident, contain the threat, and remediate affected systems.
- Threat Hunting: Security professionals proactively search for IOCs to uncover hidden threats or vulnerabilities before they cause damage. This practice, known as threat hunting, helps organizations stay one step ahead of cyber adversaries.
- Information Sharing: Sharing IOCs within the cybersecurity community and across organizations enhances collective defense efforts. Security experts can help others protect their systems effectively by disseminating information about known threats.
- Security Automation: IOCs can be integrated into security tools and systems to automate threat detection and response. Automated systems can continuously monitor network and system activity, identifying and mitigating threats in real-time.
How are IOCs generated?
- Collection of Data: Generating IOCs begins with collecting relevant data. This data can come from various sources within an organization’s network and systems, including logs, network traffic, endpoint activity, and security sensors.
- Data Sources for IOCs: Data sources for IOCs encompass a wide range of information, such as firewall logs, antivirus alerts, intrusion detection system (IDS) alerts, and endpoint logs. External threat intelligence feeds, open-source threat feeds, and incident reports can provide valuable data for generating IOCs.
- The Role of Threat Intelligence: Threat intelligence is critical to IOC generation. It involves the continuous monitoring and analysis of emerging threats and vulnerabilities. Threat intelligence feeds provide information on the latest attack tactics, techniques, and procedures (TTPs), which can be used to create IOCs effective against evolving threats.
- Manual vs. Automated IOC Generation: IOC generation can be manual or automated. Manual generation involves cybersecurity analysts manually analyzing data, identifying patterns, and creating IOCs based on their expertise. Automatic generation, on the other hand, relies on security tools and algorithms to identify and develop IOCs automatically. A combination of both approaches is often employed for comprehensive IOC coverage.
 Common Examples of IOCs
Common Examples of IOCs
- IP Addresses: Suspicious or known malicious IP addresses are common IOCs. These addresses may be associated with command and control servers, malware hosts, or known harmful sources.
- URLs and Domains: Malicious URLs and domains are frequently used in phishing campaigns and malware distribution. Monitoring and blocking such IOCs can prevent users from accessing harmful websites.
- File Hashes: File hashes, such as MD5, SHA-1, and SHA-256, are used to uniquely identify files. Malicious files can be detected by comparing them to known malicious file hashes.
- Registry Keys and System Artifacts: In the case of host-based IOCs, suspicious or unauthorized registry keys and system artifacts can be indicators of compromise. Malware often leaves traces in the system’s registry.
- Behavioral Patterns: Unusual or suspicious behavior within a network or system can serve as an IOC. This includes abnormal login activity, data exfiltration, and unauthorized access attempts.
Detecting and Responding to IOCs
- The Importance of IOCs in Threat Detection: IOC intrusion detection system are fundamental for identifying and detecting cyber threats. They enable organizations to spot anomalies and signs of compromise promptly and strengthen network traffic.
- Utilizing Security Information and Event Management (SIEM) Systems: SIEM systems are instrumental in IOC detection. They collect and analyze data from various sources, allowing real-time IOC monitoring and alerts.
- Incident Response Strategies: When IOCs are triggered, cybersecurity incident response strategies come into play. These strategies include isolating affected systems, conducting forensic analysis, and applying remediation measures to contain and eradicate threats.
Conclusion
Throughout this blog, we’ve explored the critical role of Indicators of Compromise (IOCs) in cybersecurity. These digital breadcrumbs are essential in identifying, detecting, and responding to cyber threats. IOCs empower organizations to safeguard their digital assets and sensitive data by providing early warning signs and actionable intelligence.
The threat landscape is in a constant state of flux. As technology advances, so do the tactics of cyber adversaries. Threat actors continually adapt and refine their methods, making it imperative for cybersecurity professionals to stay ahead of the curve. IOCs are invaluable in this ever-evolving battle, helping us detect new attack vectors and emerging threats.
Cybersecurity is not a one-and-done endeavor. It’s an ongoing process that demands vigilance and adaptation. Organizations must continually update their defenses and response strategies as cyber threats become more sophisticated. IOCs provide a proactive means, enabling us to respond rapidly to new threats and vulnerabilities.
Protected Harbor: Your Trusted Partner in Cybersecurity
In the ever-competitive landscape of managed IT services and cybersecurity providers, one company stands out as a trusted partner for organizations seeking top-notch protection—Protected Harbor. With a commitment to cutting-edge technology and a team of experts dedicated to staying ahead of emerging threats, Protected Harbor has earned its reputation as one of the premier cybersecurity service providers in the United States.
Whether you’re a small business looking to fortify your defenses or a large enterprise seeking comprehensive cybersecurity solutions, Protected Harbor offers a range of services tailored to your needs. Protected Harbor is your reliable ally in the ongoing battle against cyber threats, from threat detection and incident response to proactive threat hunting and compliance management.
Don’t leave your organization’s cybersecurity to chance. Partner with the experts at Protected Harbor and ensure the safety and integrity of your digital assets. To learn more about our services and how we can enhance your cybersecurity posture, visit our website or contact us today.
Partner with Protected Harbor, and let’s secure your digital future together.





 Myth #3: Two-Factor Authentication is Infallible – No Need for Additional Security Measures
Myth #3: Two-Factor Authentication is Infallible – No Need for Additional Security Measures



 Threat Detection and Response Best Practices
Threat Detection and Response Best Practices




 Implementing Zero Trust Security
Implementing Zero Trust Security

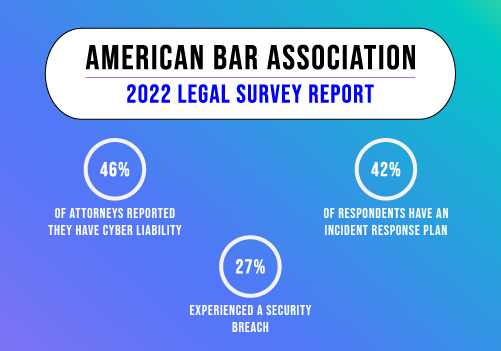



 6. Regularly Update Software and Systems
6. Regularly Update Software and Systems

 with privacy laws such as the GDPR and CCPA. However, like with cybersecurity tools, these technologies must be implemented as part of a comprehensive privacy strategy to really be effective.
with privacy laws such as the GDPR and CCPA. However, like with cybersecurity tools, these technologies must be implemented as part of a comprehensive privacy strategy to really be effective.

 Best Practices for Managing Data Security and Privacy Concerns in Cloud Computing
Best Practices for Managing Data Security and Privacy Concerns in Cloud Computing