Top 10 Cybersecurity Trends for 2025 and How to Prepare

Top 10 Cybersecurity Trends for 2025 and How to Prepare
As we step into 2025, the cybersecurity landscape continues to evolve, presenting both unprecedented opportunities and escalating challenges. Technology is advancing at breakneck speed, empowering businesses and individuals to thrive in the digital realm. Yet, this progress is matched by increasingly sophisticated cyber threats that threaten trust, reputation, and the very survival of organizations.
Cybersecurity is no longer just an IT concern; it has become a business-critical priority. The threats we face today are real, persistent, and targeted. Whether you’re leading cybersecurity efforts at a multinational enterprise, managing IT at a mid-sized firm, or securing a small business network, the time to act is now. Preparing for these challenges isn’t merely about keeping up with trends—it’s about anticipating risks and building resilient systems.
In this blog, we’ll explore the top 10 cybersecurity trends for 2025 and how to prepare, actionable steps to implement. Let’s dive in.
1. Continuous Threat Exposure Management (CTEM)
CTEM is becoming a game-changer in cybersecurity. This structured approach proactively measures and reduces an organization’s exposure to cyber threats. CTEM identifies vulnerabilities, simulates attacks, and prioritizes remediation to mitigate risks before attackers can exploit them.
How to Prepare:
- Implement a CTEM framework in your organization.
- Use automated vulnerability scanners to identify weak points.
- Run threat simulations regularly and prioritize remediation based on the impact and likelihood of vulnerabilities.
Protected Harbor Advantage: Our proactive approach integrates CTEM strategies into a broader cybersecurity framework, ensuring that vulnerabilities are identified and addressed before they can become critical threats.
2. Rise of AI-Powered Cyber Attacks
Artificial Intelligence is a double-edged sword. While AI is empowering defenders, attackers are also leveraging it to automate attacks, bypass defenses, and deploy convincing phishing schemes. AI-powered deepfake technology is creating more effective social engineering scams, further amplifying risks.
How to Prepare:
- Invest in AI-driven cybersecurity tools that detect anomalies and prioritize threats in real-time.
- Train your teams to understand AI’s role as both a defense and a potential threat.
- Partner with cybersecurity providers who specialize in AI threat mitigation.
Protected Harbor Advantage: We leverage AI tools to adaptively secure systems while continuously monitoring for evolving AI-driven threats.
3. Quantum Computing Threats
Quantum computing, while a promising technology, poses a significant threat to encryption standards. Current encryption methods could become obsolete as quantum computing matures, potentially leading to a “quantum apocalypse.”
How to Prepare:
- Begin transitioning to quantum-resistant encryption protocols.
- Collaborate with cybersecurity vendors to stay informed on post-quantum cryptography advancements.
Protected Harbor Advantage: We are actively integrating quantum-resistant technologies into our solutions to future-proof your digital assets.
4. Increase in Ransomware-as-a-Service (RaaS)
Ransomware is evolving into a lucrative business model. With RaaS kits available on the dark web, even low-skilled cybercriminals can launch devastating attacks. The average ransom payment increased by 58% in 2024, reflecting the growing sophistication and impact of ransomware.
How to Prepare:
- Test your data backup and recovery strategies regularly.
- Implement email phishing training and network segmentation.
- Explore cyber insurance policies to offset financial losses.
Protected Harbor Advantage: We specialize in ransomware defense with advanced backup systems and network segmentation strategies to minimize downtime and ensure quick recovery.
5. Regulatory Compliance Tightens
Governments worldwide are introducing stricter data protection regulations, making compliance more challenging. From the U.S. federal privacy law to India’s new Digital Personal Data Protection Act, organizations are under greater scrutiny.
How to Prepare:
- Audit your compliance posture regularly.
- Use automation tools to track evolving regulations.
- Partner with legal and cybersecurity experts to ensure adherence.
Protected Harbor Advantage: We simplify compliance by providing automated tracking tools and expert support to ensure your business remains secure and regulation-ready.
 6. Cloud Security Becomes Paramount
6. Cloud Security Becomes Paramount
Cloud adoption is surging, with spending expected to exceed $1 trillion by 2026. However, misconfigurations and weak access controls continue to make the cloud a prime target for attackers.
How to Prepare:
- Conduct regular cloud security assessments.
- Adopt Zero Trust Architecture and robust Identity and Access Management (IAM) solutions.
Protected Harbor Advantage: We implement cutting-edge cloud security solutions, including Zero Trust policies and API protections, to safeguard your cloud environments.
7. Human Error Remains a Major Risk
Despite advanced tools, human error is responsible for 95% of breaches. Weak passwords, falling for phishing emails, and mishandling sensitive data remain common issues.
How to Prepare:
- Invest in ongoing security awareness training for employees.
- Use gamified training tools to keep engagement high.
- Deploy multi-factor authentication (MFA) to reduce risk.
Protected Harbor Advantage: Our comprehensive training programs are designed to build a security-conscious workforce while implementing technologies like MFA to mitigate human errors.
8. Cyber Insurance Gains Momentum
As businesses seek financial protection from breaches, cyber insurance is becoming a must-have. However, insurers are demanding evidence of strong security practices before offering coverage.
How to Prepare:
- Maintain thorough documentation of your cybersecurity policies.
- Regularly update your security measures to meet insurers’ requirements.
Protected Harbor Advantage: We assist businesses in meeting insurance requirements by implementing best-in-class security measures and providing detailed documentation.
9. IoT Devices: A Growing Threat
The number of IoT devices is expected to reach 30.9 billion by 2025, but many of these devices lack robust security features. This makes them easy targets for attackers.
How to Prepare:
- Secure IoT devices with strong authentication and network segmentation.
- Use IoT-specific security solutions to monitor device activity.
Protected Harbor Advantage: We provide IoT-specific security solutions to protect every connected device within your organization.
10. Supply Chain Attacks on the Rise
Supply chain attacks are becoming increasingly common. Threat actors target vendors to infiltrate larger organizations, as seen in recent high-profile breaches like SolarWinds.
How to Prepare:
- Vet suppliers’ security practices thoroughly.
- Include security clauses in vendor contracts and monitor third-party access.
Protected Harbor Advantage: We help businesses secure their supply chains by offering visibility tools and best practices for managing third-party risks.
How to Prepare: A Proactive Cybersecurity Strategy
Preparation is the cornerstone of any effective cybersecurity strategy. The ever-evolving threat landscape requires organizations to move beyond reactive measures and adopt a proactive approach. Here’s how to prepare:
- Adopt a Zero Trust Framework: Assume no user or device is trustworthy by default. Verify every access request and enforce least-privilege principles.
- Invest in Continuous Monitoring: Use advanced tools to monitor network traffic, detect anomalies, and respond to threats in real-time.
- Prioritize Incident Response: Develop and regularly test an incident response plan to ensure your organization can recover quickly from a breach.
- Leverage Proactive Services: Partner with managed service providers (MSPs) like Protected Harbor, which focus on identifying and mitigating threats before they become problems.
- Embrace Automation: Automate repetitive security tasks like patch management and vulnerability scans to free up resources for strategic initiatives.
Conclusion: Stay Ahead with Protected Harbor
Cybersecurity in 2025 requires a proactive, integrated, and adaptive approach. At Protected Harbor, we don’t just respond to threats—we anticipate them. By staying ahead of trends like AI-powered attacks, quantum threats, and RaaS, we empower businesses to secure their operations and build trust.
Our out-of-the-box approach combines advanced tools, proactive strategies, and expert guidance to address your unique challenges. Whether you need to enhance your cloud security, defend against ransomware, or secure IoT devices, we’re here to help.
Take the first step today. Contact us to learn how Protected Harbor can transform your cybersecurity strategy. Let’s build a safer digital future together.








 Detecting Zero-Day Vulnerabilities
Detecting Zero-Day Vulnerabilities







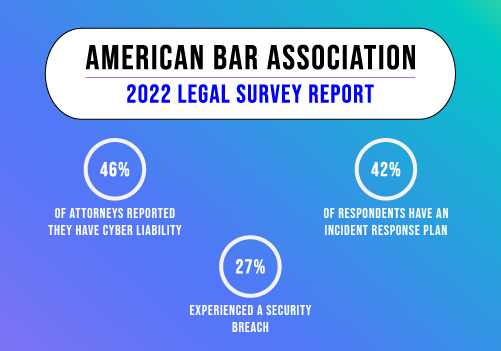











 1. Bridgestone
1. Bridgestone