How to Prevent Malware

How to Prevent Malware
Whether it’s a new album from our favorite band, an application to make our browser run faster, or a new computer game we want to check out, we are in a state of constant downloading. We can leave ourselves open to cybercriminal attacks if we aren’t vigilant about what we download.
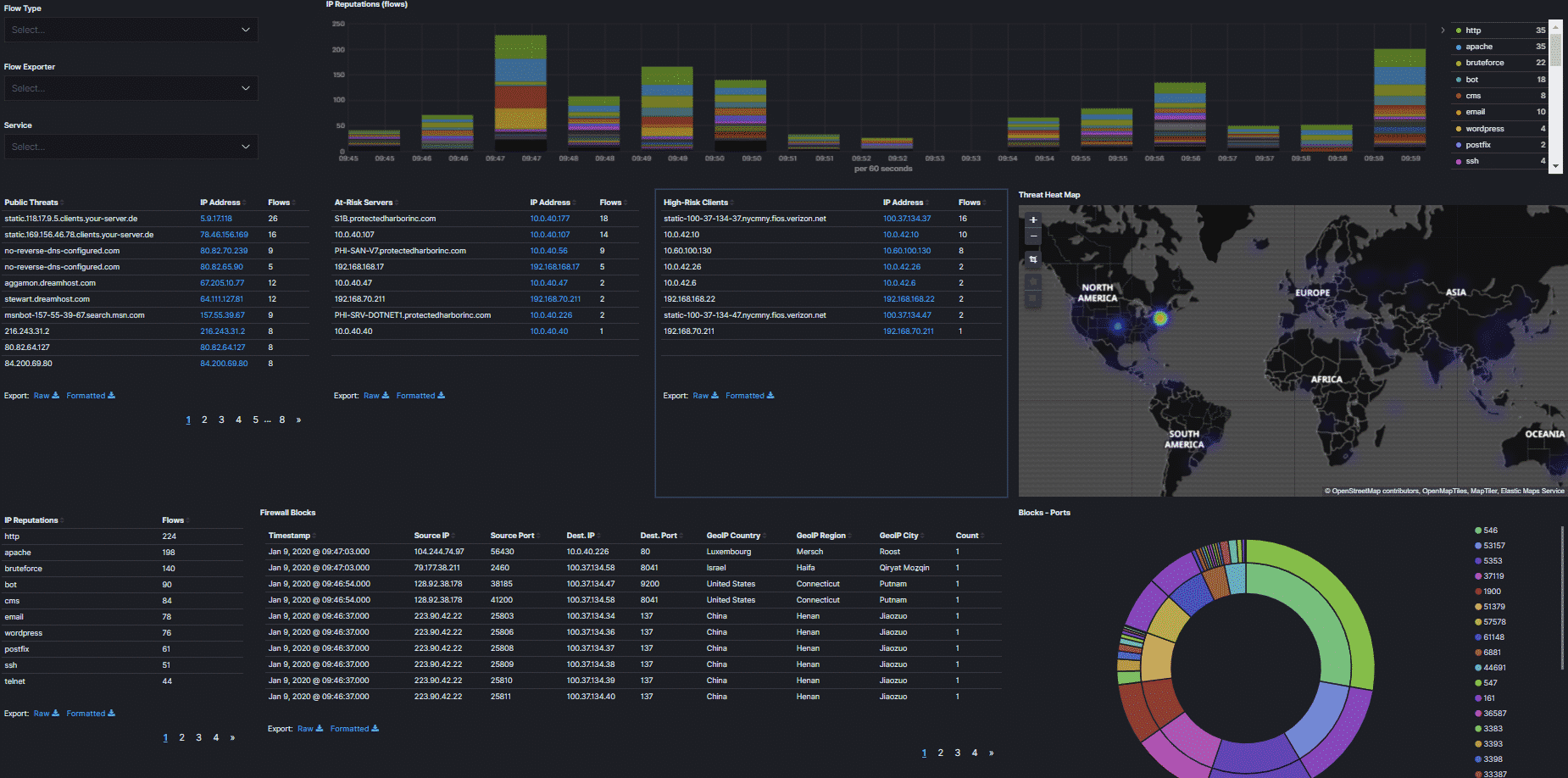
When our gear starts behaving strangely, our first thought is that it’s a virus. Though a virus is always a possibility, the problem is more frequently known as malware. The malware was the most concerning cyber threat targeting enterprises, according to a poll of global IT security decision-makers conducted in November 2020. Phishing and ransomware were tied for second place with a relative score of 3.99 on a five-point scale.
This article will discuss how to prevent malware and highlight ways how to prevent malware. Let’s get started.
The Most Common Ways You Can Get Malware
Malware is a type of software program that is designed to damage or disable computers and computer systems. It includes computer viruses, worms, Trojan horses, ransomware, spyware, and adware. Malware can cause a loss of productivity, revenue, and reputation for businesses. In some cases, malware can lead to data theft or identity theft.
One of the most common types of malware is a virus. A virus is a small code that attaches itself to another program or document so it can spread from one computer to another without being detected by security software. Viruses are often sent through legitimate email messages but contain malicious attachments or links to malicious websites.
Malware is a huge problem, and it cannot be easy to protect yourself. Some people think they’re safe because they don’t install software from the internet, and that’s true, but malware can still get on your computer in other ways.
The most common ways you can get malware:
- Downloading free software (malvertising)
- Opening an infected attachment in an email
- Visiting a malicious website
- Sending files to someone via email or instant messaging
Impact of Malware
Malware may also include spyware and adware programs that collect information about your online activity and display unwanted or intrusive advertisements on your screen. Some malware is designed to steal your personal information, such as credit card numbers or passwords.
Often, malware is installed without your consent when you visit an infected website or open an email attachment containing a virus. Once installed, malware can perform any number of functions, including:
- Stealing your personal information.
- Stealing money from your bank account.
- Disabling essential system files so that you cannot use your computer.
Do I Need to Clean My Network or Computer for Malware?
You can protect yourself from malware in several ways. The first is personal vigilance. You should avoid clicking on links, downloading files from unknown sources, and visiting websites with a reputation for containing malicious code. Most importantly, ensure all your software is updated, including your operating system and browser.
The second protection method uses protective tools such as firewalls and antivirus software. These tools can monitor your network traffic and detect any suspicious behavior coming from your computer or network, then block it before it has a chance to do any damage.
Steps to Protect Your Computer from Malware
So, what can you do to protect yourself against common viruses like ransomware, phishing, and cryptojacking?
A strategy is outlined below.
1. Rely Only On Secure Networks (Encrypted)
If you’re using an unsecured Wi-Fi network, someone could easily intercept your data as it moves between your computer and your site. This includes sensitive information like passwords and credit card numbers.
2. Employ Browser Common Sense
Browsers are one of the most common ways malware gets onto your computer. Many sites try to trick you into clicking on links or downloading files that contain malware. Be careful when browsing online, and avoid clicking on links in emails from unknown senders.
3. Take Care of Your Personal Information
The most important thing to prevent malware from infecting your device is to keep a tight grip on your personal information. This means never sharing personal details over email or social media platforms. It would be best if you also avoided downloading apps from unverified developers and websites, as they could be hiding malicious code inside their programs.
4. Stay Up-to-Date on the Latest Attacks
Maintain your operating system, any third-party applications installed on your computer, and any antivirus software installed on your computer to have the latest protection against new threats that may be around the corner.
5. Use Antivirus Software
While not foolproof, antivirus software can detect and block some types of malware at entry into your device or system. But even if it does catch a virus, it won’t remove it from your computer because it doesn’t have access to all areas of the operating system where there are viruses.
6. Don’t Click Suspicious Links or Attachments
It can be hard not to click on suspicious links or attachments in emails or text messages, especially if they appear to come from someone you know. However, if an email or text message looks strange, don’t open it! Malware can spread through email attachments and links that take you to phishing websites, where criminals try to trick users into giving up their personal information.
7. Use Strong Passwords
Make sure you use a different password for each account — including gaming accounts. At least eight characters should be used with a combination of numbers and letters that aren’t found in the dictionary or on a keyboard. It shouldn’t be easy to guess your birthday, family member’s name, or pet’s name.
8. Configure Regular Scans and Monitor Settings
Malware can be distributed using various methods, including email attachments, social media links, and fake websites. To stop malware from infecting your device, you need to configure it for scanning regularly. This will help identify any threats before they cause damage to your system. You should also configure your network settings to detect any changes in traffic patterns that might indicate an attack.
9. Always Update Your Operating System
You must keep your operating system up-to-date because new updates often contain patches for existing vulnerabilities that malware developers could exploit. If you don’t update regularly, it leaves your device susceptible to attacks by cybercriminals who may use these vulnerabilities against users with outdated systems.
Final Words
Infections with malware can be fatal for businesses. Malware can seriously harm your finances and reputation by disrupting essential procedures and stealing or encrypting vital data. Use the suggestions above to safeguard you and your company against malware attacks. Additionally, make sure you regularly isolate the backup of your data so that you can restore it from a backup if your environment becomes infected with malware. You should always ensure you download software from trusted sites only.
At Protected Harbor, we are a team of cybersecurity experts who can assist your business in safeguarding critical data from cyberattacks and data breaches. We offer 24/7 monitoring, isolated backups, endpoint security, network security, and advanced threat detection to protect your organization against malware, ransomware, and other cyber threats. Our expert engineers will work with you to develop a customized network security solution that meets your organization’s needs. From top to bottom, we ensure that your network is secure and protected against the latest cyber threats.
Contact Protected Harbor today for tools and free IT consultation regarding malware prevention and detection.











 Keeping Your Passwords Safe and Protected
Keeping Your Passwords Safe and Protected