Why is IT Experience Important for Businesses
Why is IT Experience Important for Businesses?
The role of IT in modern business cannot be underestimated. Companies now must pay attention to the importance of information technology (IT). In this role, every business must own and implement IT systems. The failure to innovate means rejecting best practices.
You can’t expect to keep up with the competition if you don’t give your company an edge in technology adoption. The fact should be noticed – with the proper IT solutions. Your organization could succeed entirely.
The annual value of the global information technology (IT), business services, and IT services markets exceeds USD 1 trillion. The Americas area will account for most of the sales in 2021 with 555 billion US dollars. After dropping revenues in 2020 due to the coronavirus pandemic, the market is predicted to see rising revenues during the following four years. ~Statista
Even If you’re a small business owner, you might know how important technology is, but need help understanding it. We’ll tell you the business rechnology benefits and what technology can do for your business and why it’s essential.
What is Information Technology in Business?
The term “IT” is often used in today’s business world. This is simply because of the importance of IT in business. Information Technology is a broad term that covers a range of topics, including information systems, computer networks, database management, and software applications.
In general, Information Technology is applying computer technology to support business operations. Word processing and spreadsheet software are the most common IT applications; however, many other types are also used in businesses today.
Generally, a wide range of technologies and infrastructure strategies that work in concert shape the IT services sector. The use of technologies like artificial intelligence (AI) and machine learning (ML) in business solutions and a rise in the demand for IT security measures like zero trust frameworks are a few of these trends.
Why is IT experience important? Information technology has become the backbone of business because it can help companies do things faster and with less effort. It allows companies to communicate with customers, employees, and suppliers more quickly; it helps companies coordinate operations across multiple locations and time zones; it enables companies to share information in real-time with customers or employees who need it, and it provides access to data that would otherwise be difficult or impossible for a company to collect.
 Why is IT Important for Businesses?
Why is IT Important for Businesses?
The IT department is the backbone of any business. It has a direct impact on the productivity and efficiency of your business.
Simplifying Employee Communication
IT infrastructure enables employees to conduct their work efficiently and effectively. Adequate IT infrastructure can make all the difference between a thriving and a failing business. It also helps in improving employee communication as well as collaboration with each other.
Enhancing Productivity
An efficient IT infrastructure allows you to focus on core competencies and critical activities, which help you in enhancing productivity significantly. You can also focus on business technology benefits, innovation and creativity, which are essential for your company’s growth.
Better Data Management
Data management is one area where an efficient IT infrastructure helps you immensely. With proper data management, you can analyze past data and use it to shape plans for your business. A good IT infrastructure ensures that all critical data remains safe. This provides no loss of valuable information due to unforeseen circumstances or accident-related failure of data files, hard drives, etc.
Improving Financial Management
IT makes it easier to manage your finances by automating all your financial transactions. You can also easily monitor and analyze your financial data, which helps you make better decisions about where to spend money, saving time and money in the long run.
Maintaining Network Security
Your network is one of the most vulnerable areas in your organization. IT personnel can help protect it from hackers, viruses, malware, and other threats by developing security policies and implementing them promptly. This ensures that your data remains safe and secure at all times.
Boosting Marketing Campaigns
In today’s fast-paced world, you must constantly be on your toes to survive this cutthroat competition. You must stay caught up with competitors if you want to maintain your position in the market. This is where IT comes into play by offering you an array of tools that will help you streamline your marketing campaigns and give them the boost they need.
Management of Cloud-Based Solutions
Today, businesses have started adopting the cloud computing model for their IT infrastructure needs. This allows them to access all their data anytime and from anywhere in the world. This system will enable businesses to easily manage their entire information technology infrastructure by deploying just one application across multiple devices or locations. This will help them track down what’s happening with their systems in real-time and minimize downtime if there are any issues with the system.
Future of Information Technology in Business
Businesses increasingly rely on information technology (IT) to run efficiently and effectively. Companies use IT to improve the quality of their services and products, reduce costs and increase revenues.
According to Statista, there will be over 15 billion mobile devices in use in 2021, with 18.22 billion projected by 2025. According to Zippia, the smartphone market is growing at a CAGR of 16.4% on a global basis.
Why is IT experience important? When planning for the future, it’s essential to consider the impact of technology. Introducing new technology has always been a game-changer in the business world and will continue to be so.
In recent years, there’s been a lot more focus on “big data” and how businesses can use it. The amount of data available today is staggering, yet companies are only scratching the surface of what they can do with it.
Businesses are becoming more dependent on IT systems for day-to-day operations. This is because these systems provide a better way of managing business processes than using manual methods.
In addition, the global economy has become more digitized. It has led to the emergence of new technologies such as artificial intelligence (AI), robotics, cloud computing, and Big Data analytics, improving productivity levels in businesses across all sectors.
Final Words
Overall, businesses need to implement a strategy for IT, with priorities and plans in place. There are many different moving parts to the equation, and the company must understand the importance of IT in business landscape to create an operating environment where IT can effectively serve its needs. How important is technology? The stakes couldn’t be higher—businesses that ignore technology run a greater risk of failing.
Businesses depend on rapid, reliable data and high-speed internet in today’s global economy to remain competitive. To keep your company at the cutting edge of international business, you need a business partner with the expertise to tackle the challenges of today’s technology. And at the same time, you must ensure that your company’s data remains secure. You don’t want a single mistake or oversight to risk your business’s reputation or financial stability. And you don’t have time to waste on unnecessary headaches. Finding a partner that can offer technical expertise and detailed awareness of your company’s needs can make all the difference for your business.
Protected Harbor has the right solution for you, whether you are just starting or looking to upgrade your current setup. Our expert team will work with you to discover your needs and recommend the best technology to meet those needs. We will also support your team as they get the new system up and running. We are also recognized as a top cloud computing and cybersecurity company by Goodfirm and Designrush.
Learn how the experience makes a difference. Get a free IT Audit today.






 How Safe is My Information Now?
How Safe is My Information Now?

 Common Challenges of Deploying Servers in Virtualized Environment
Common Challenges of Deploying Servers in Virtualized Environment

 Challenges of Data Center Management
Challenges of Data Center Management



 Cybersecurity Risks and Solutions
Cybersecurity Risks and Solutions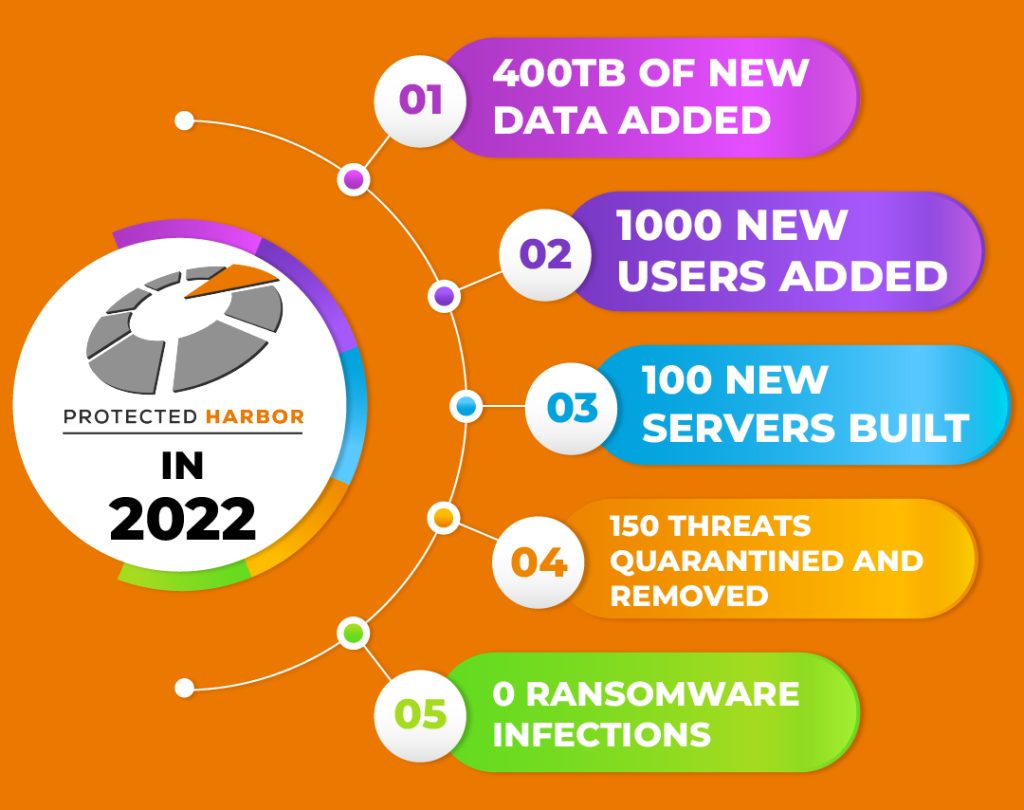

 Data as a Service – Everything You Need to Know
Data as a Service – Everything You Need to Know What are the Benefits of Data as a Service?
What are the Benefits of Data as a Service?

 Best Data Center Managed Services 2022
Best Data Center Managed Services 2022

 Why is IT Infrastructure Important for Businesses?
Why is IT Infrastructure Important for Businesses?